Dundas Reports SAML application setup
Introduction
This manual shows you how to set up SSO to Dundas Reports using the SAML protocol. The configuration takes place in HelloID and requires you to send information to Dundas Reports.
Requirements:
HelloID environment
Dundas Reports environment
SSO has to be requested at Dundas Reports, this might come with additional costs.
Create or Import a Certificate
If there is no certificate yet, a certificate must be imported or created. This can be done in the HelloID Administrator Portal under Settings > Certificates. For this tutorial, we will use a self-signed certificate. Learn more about certificates here.
Application Setup
Add the Dundas Reports Application
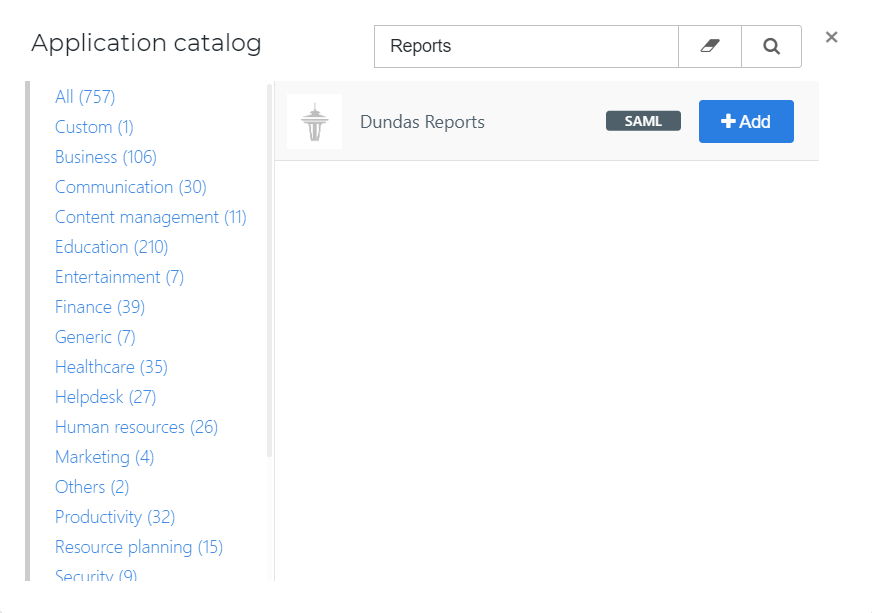
Create a new application in HelloID by navigating to Applications > Applications. Open the Application Catalog and search for "Dundas Reports". Find the SAML template, and click Add. Learn more about managing applications here.
General tab
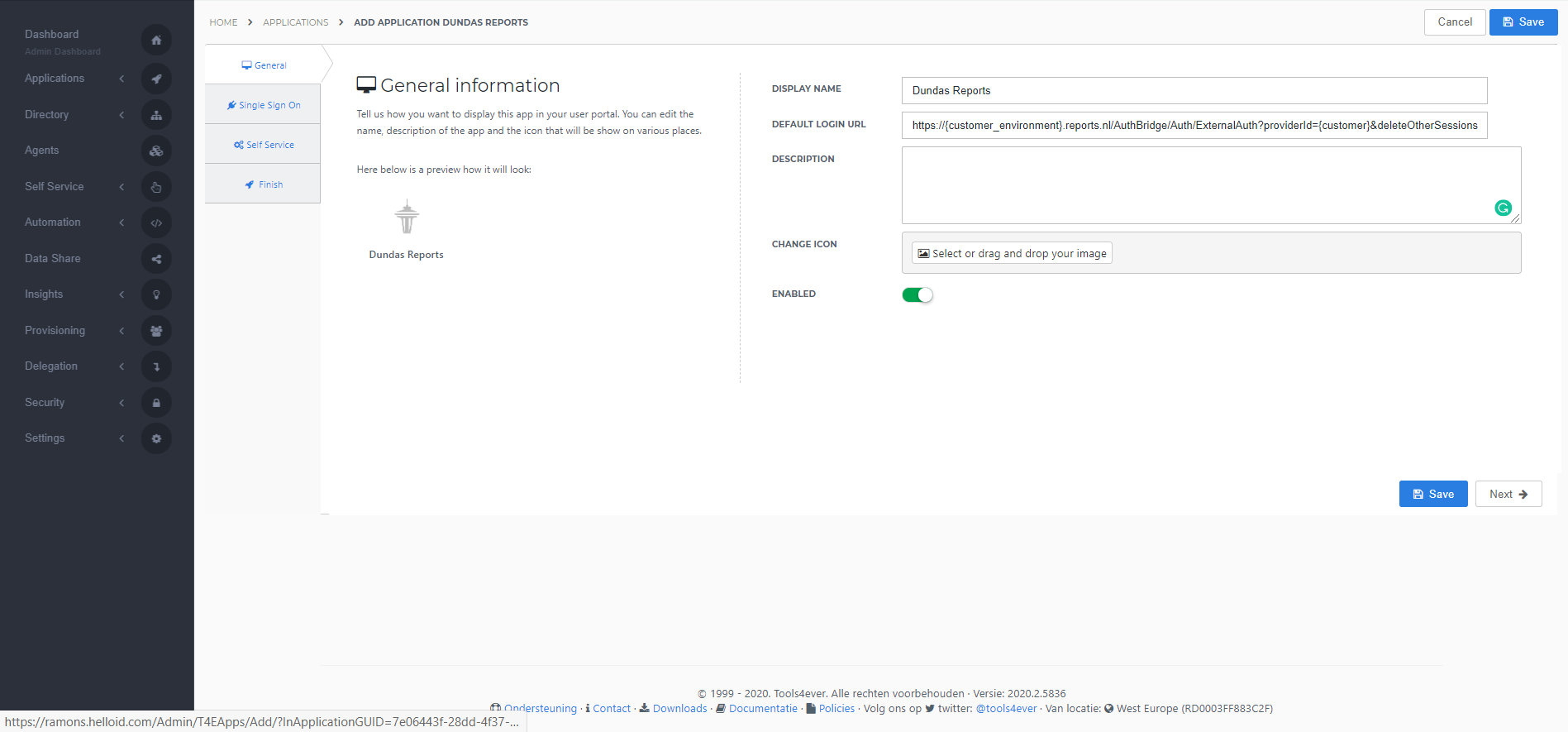
On the General tab, fill the default login URL with the Dundas Reports environment SSO URL (replace {customer_enironment} with your customer-specific Reports environment and {customer} with your customer provider ID). Optionally, you may also add a description. Click Next.
Single Sign-on tab
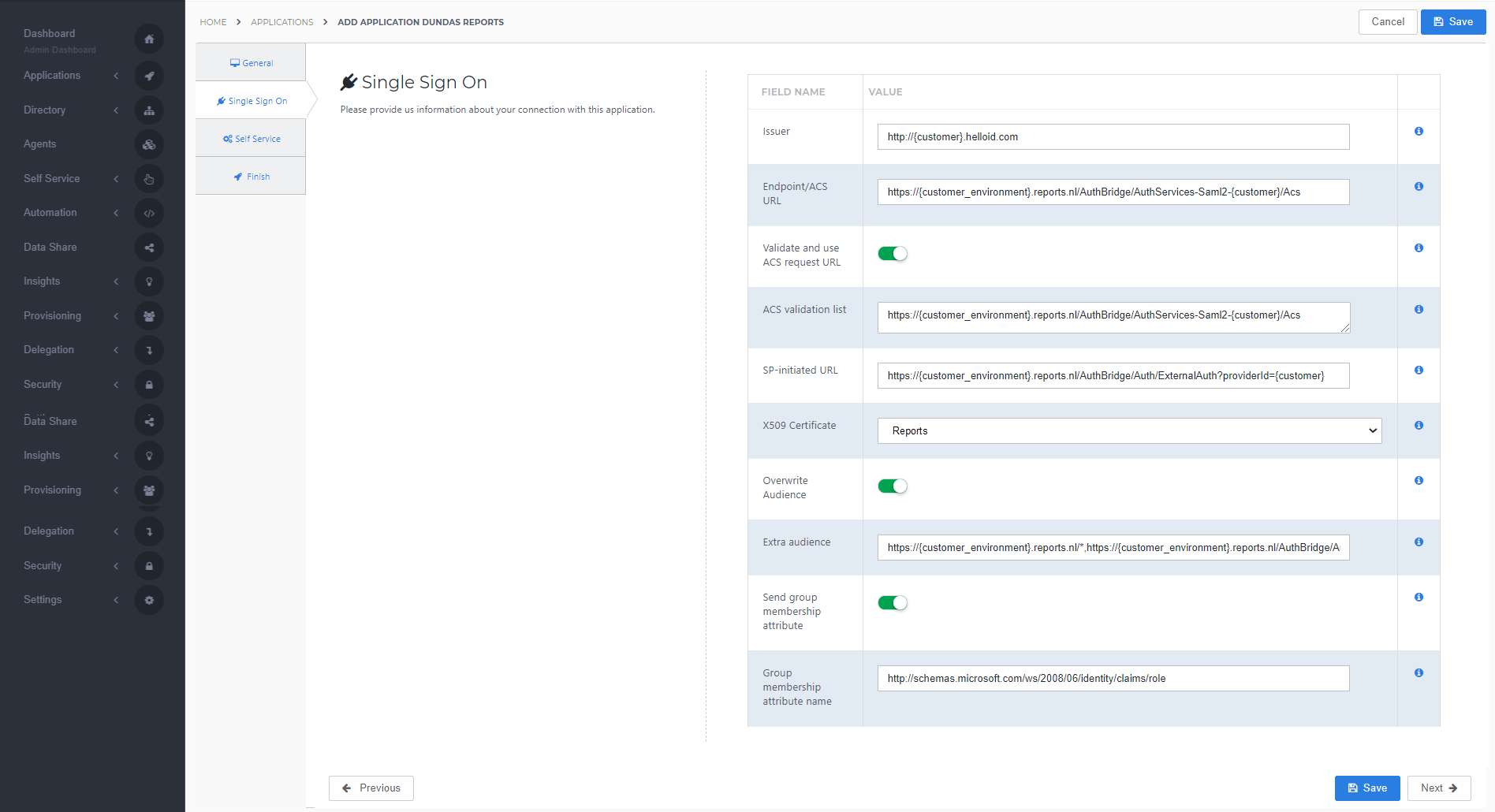
On the Single Sign-On tab, perform the following steps:
For the Issuer field, provide your HelloID domain in the format "https://{customer}.helloid.com".
Endpoint/ACS URL should be set with the ACS endpoint URL of your Dundas Reports environment in the format "https://{customer_environment}.reports.nl/AuthBridge/AuthServices-Saml2-{customer}/Acs"
Validate and use ACS request URL is always selected for security reasons.
ACS validation list should contain the URL you entered at the Endpoint/ACS URL
In the X509 Certificate dropdown, select the certificate that you created or imported previously.
The Overwrite audience should be selected.
As Extra audience enter in the following URLs (replace {customer_enironment} with your customer-specific Reports environment and {customer} with your customer provider ID):
https://{customer_environment}.reports.nl/*,
https://{customer_environment}.reports.nl/AuthBridge/AuthServices-Saml2-{customer}/Acs,
https://{customer_environment}.reports.nl/AuthBridge/,
https://{customer_environment}.reports.nl
Optionally, select the option to Send group membership attribute.
The Group membership attribute name you'll see a pre-provided URL, this is attribute has a fixed value.
Click Next.
Self service tab
On the Self Service tab, choose whether to automatically create a Self Service product, which makes the application requestable. This is optional. Click Next.
Finish tab
On the Finish tab, click Save to add the application to HelloID.
Configuring the Mapping Set
By default, the 'matching identifier' is set to the user's SAMaccountname. This is assuming the SAMAccountName is known in HelloID and matches in Dundas Reports.
If you wish to use another attribute, click here to learn more about attribute mappings.
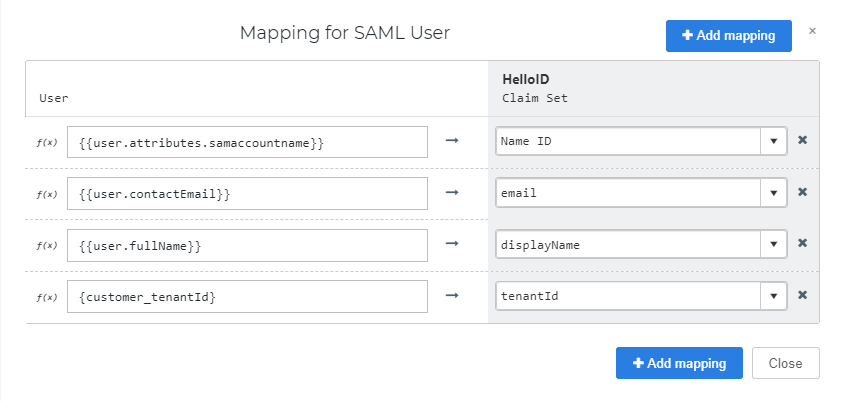
Dundas Reports requires the customer tenant ID within the SAML Response, therefore we have to change this in the mappings.
Replace {customer_tenantId} with the tenant ID of your Dundas Reports environment.
Application metadata
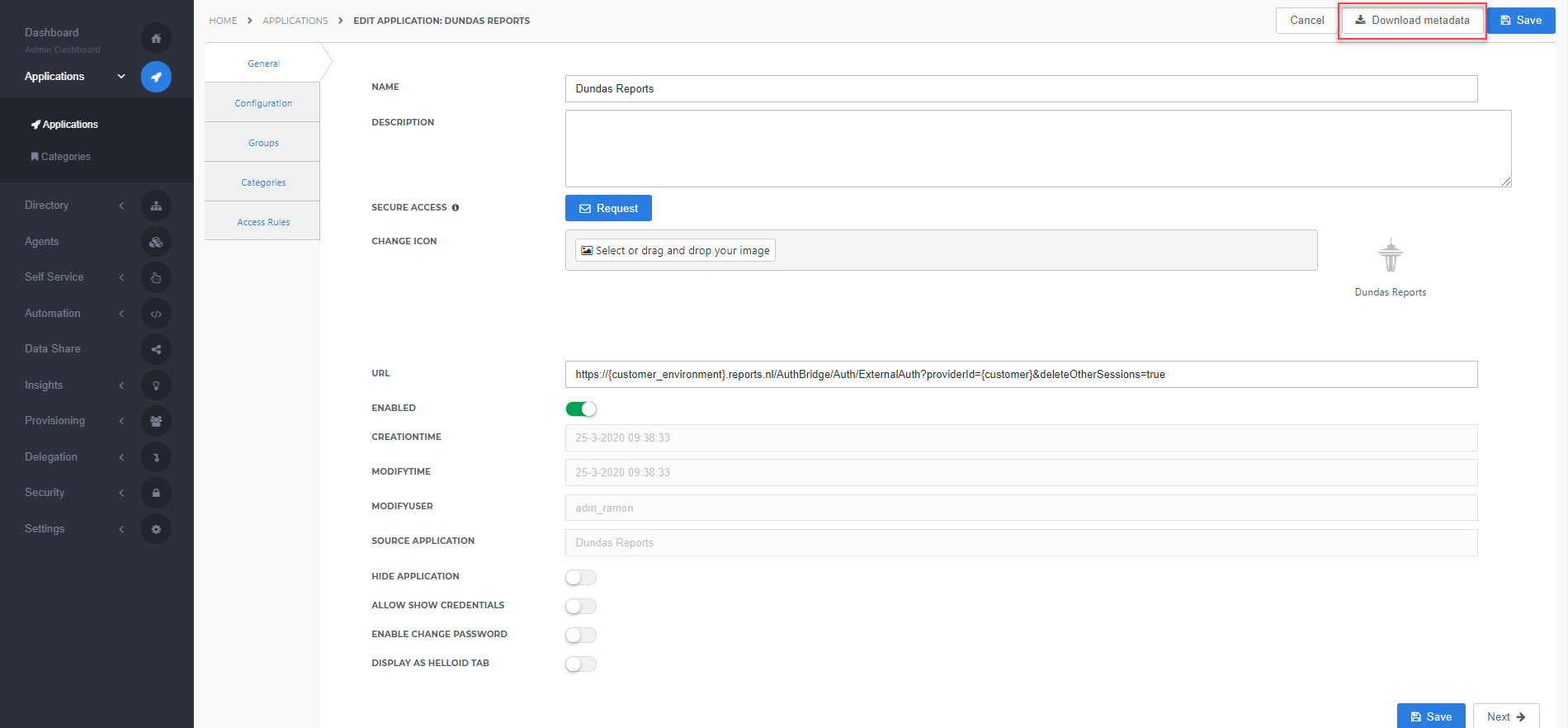
After saving the Dundas Reports application, click its Edit link on the applications overview. This will bring you to its properties page.
You now have the option to obtain the application metadata.
Dynamic Metadata (URL)
You can simply right-click Download metadata and copy the link address (something along the lines of https://enyoi.helloid.com/metadata/download?ApplicationGUID=e6e741f5-a469-4849-93f7-fe2e259a339f) at the right top of the screen.
Replace the word 'download' with 'index' in the URL to view the metadata. This URL is the Dynamix Metadata URL.
Please provide this dynamic Metadata URL to Dundas Reports.
The configuration of the HelloID application is finished.
Dundas Reports Configuration
Request SAML
In order to make the connection, Dundas Reports needs to add the connection on their side. This can be requested at Dundas Reports, this might come with additional costs.
To configure the SSO on the Dundas Reports side, they will need the following information:
Metadata URLPlease provide the dynamic Metadata to Dundas Reports
IssuerThis is the issuer you configured in the HelloID configuration earlier in the format "https://{customer}.helloid.com"
IdP X.509 Certificate
This can be found in the HelloID Metadata provided and should not be provided separately.
Dundas Reports should get this from the HelloID Metadata.
Finishing Up
The Dundas Reports application has now been added to HelloID, and a trust has been configured between Dundas Reports and HelloID. You are now free to assign the application to users within your organization and begin testing it and using it. You can learn more about managing applications and assigning permissions here.