Add a generic OpenID Connect application
For more information, see OIDC applications and the OpenID Connect Core docs.
Note
For this example, we'll create a demo OIDC application that can receive a request from the OIDC Debugger.
Go to Applications > Applications.
Click Open Application Catalog.
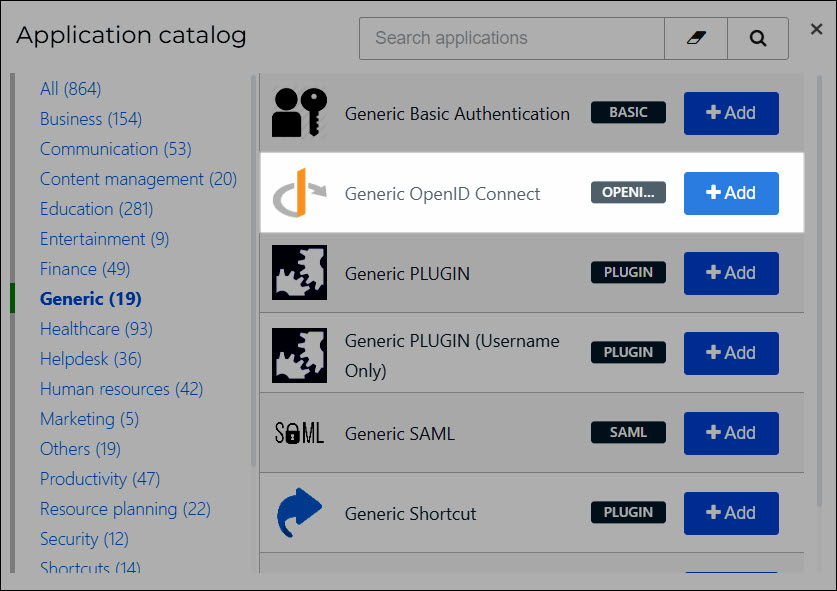
Click Generic, and then click Add for Generic OpenID Connect.
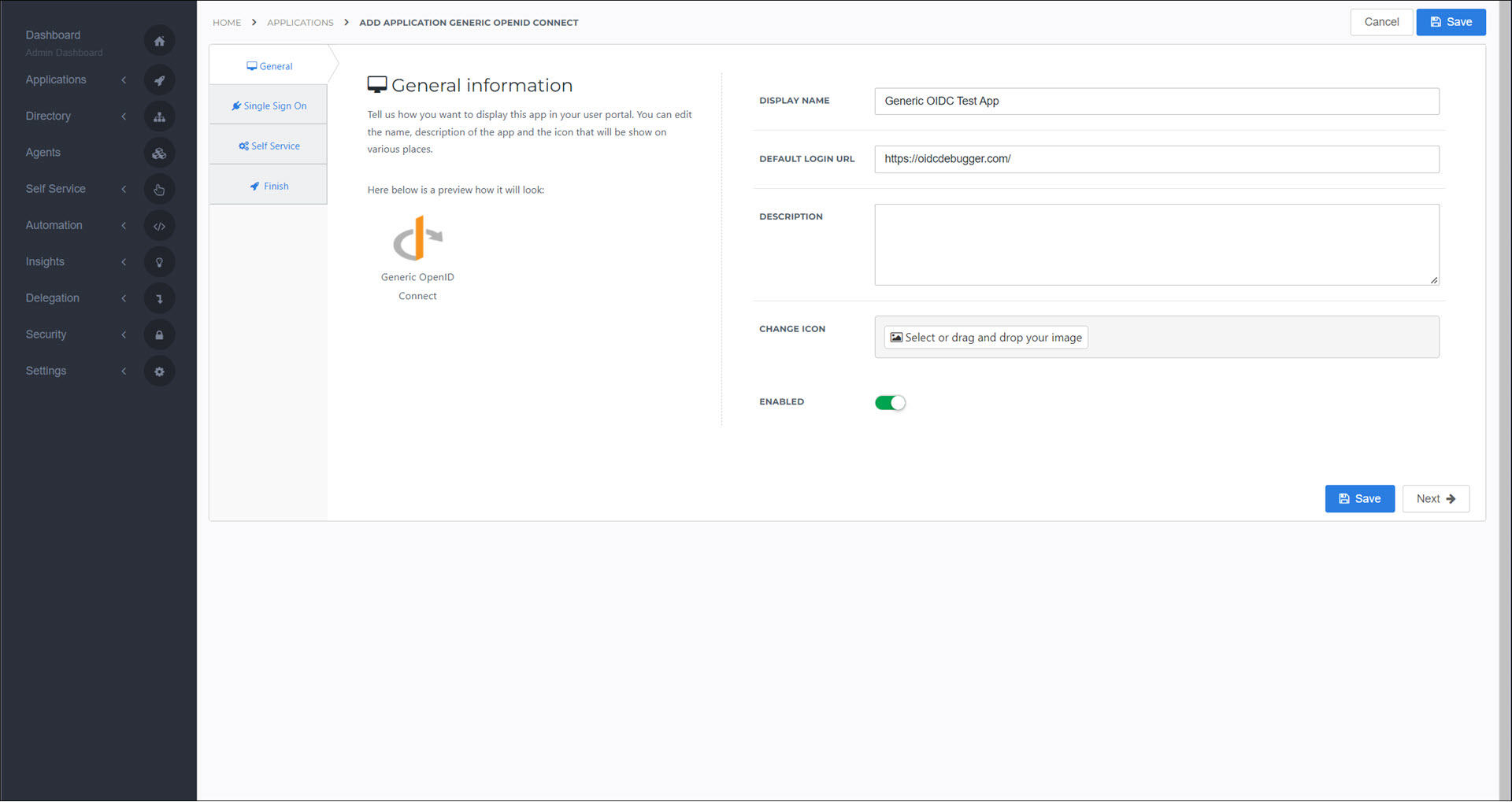
Enter a Display Name.
For this example, we'll enter
Generic OIDC Test App.Enter a Default Login URL.
For this example, we'll enter
https://oidcdebugger.com/.Optional: Enter a Description and Icon.
Click Next.
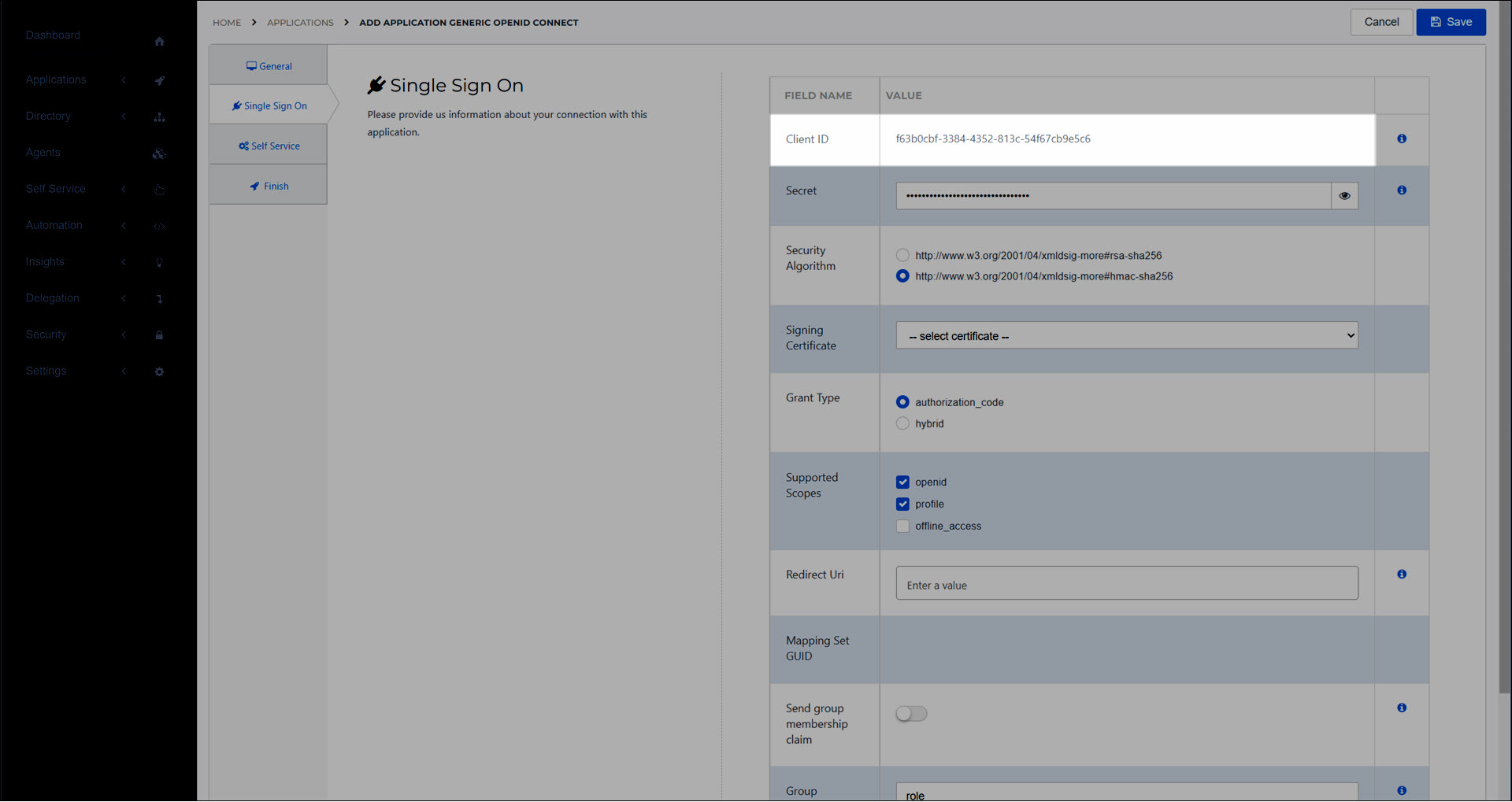
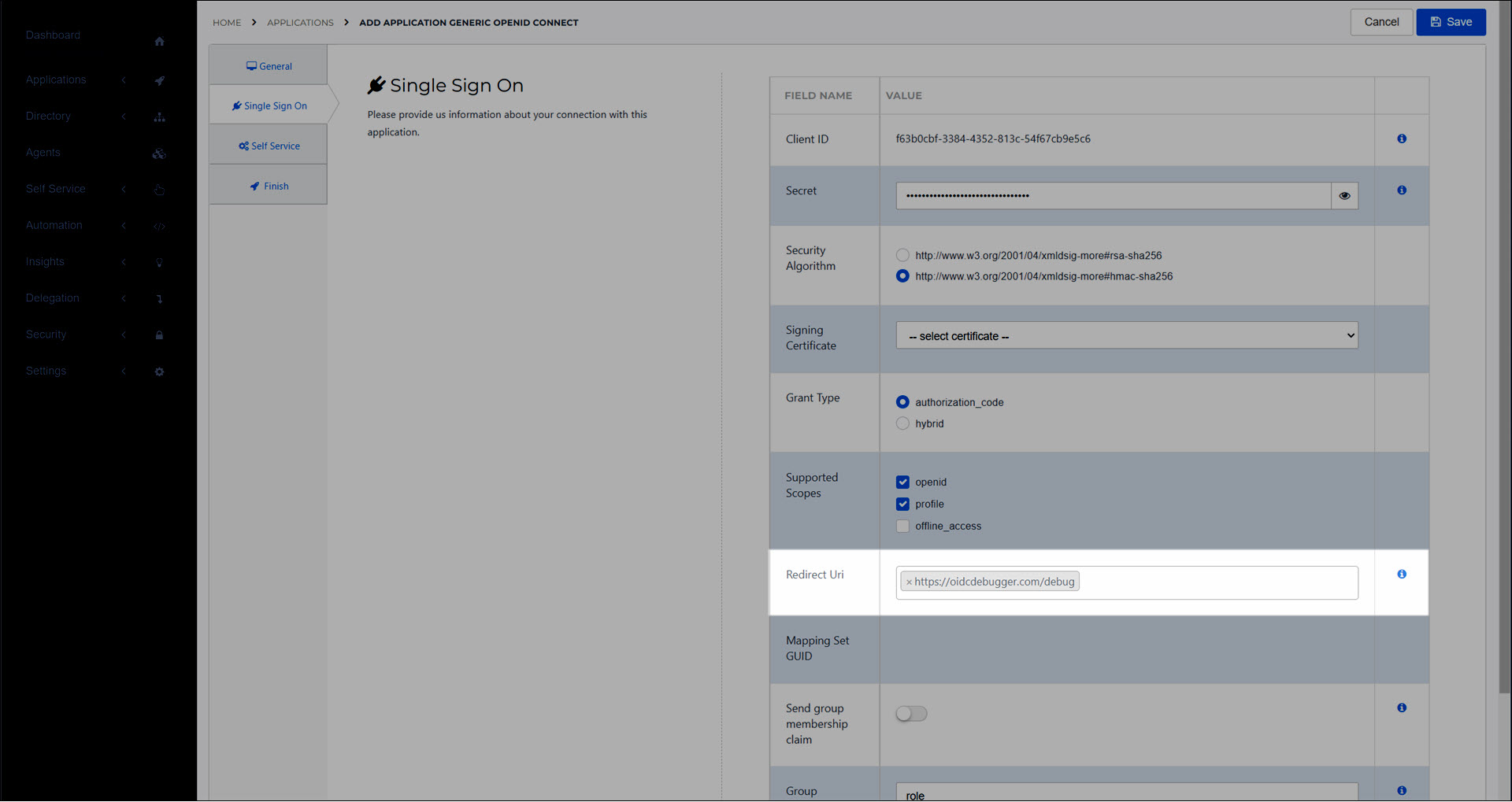
On the Single Sign On tab, configure the application's options as needed. See Application settings reference.
Copy the Client ID from HelloID into the target app.
For this example, we'll copy it into the Client ID field of the OIDC Debugger.
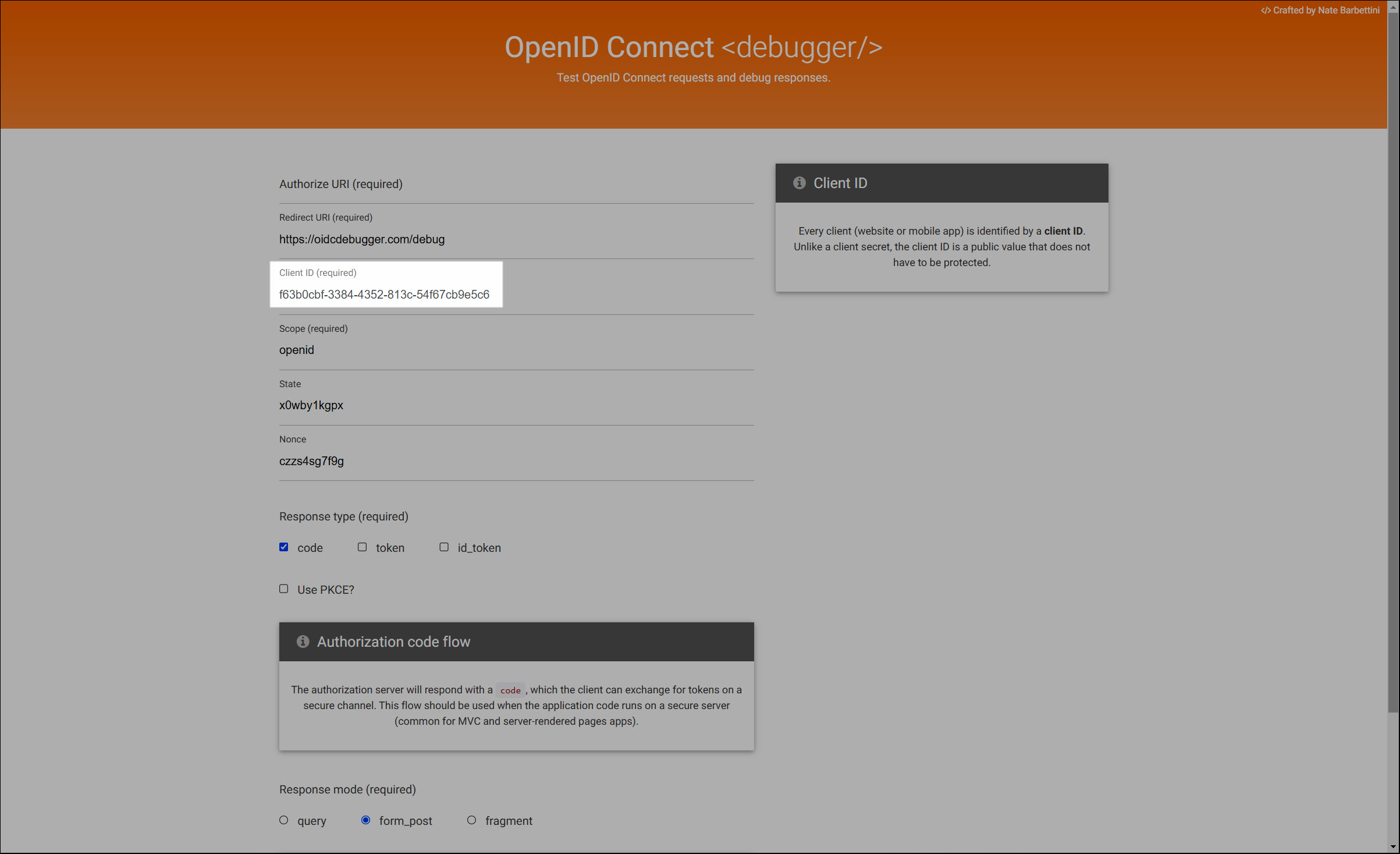
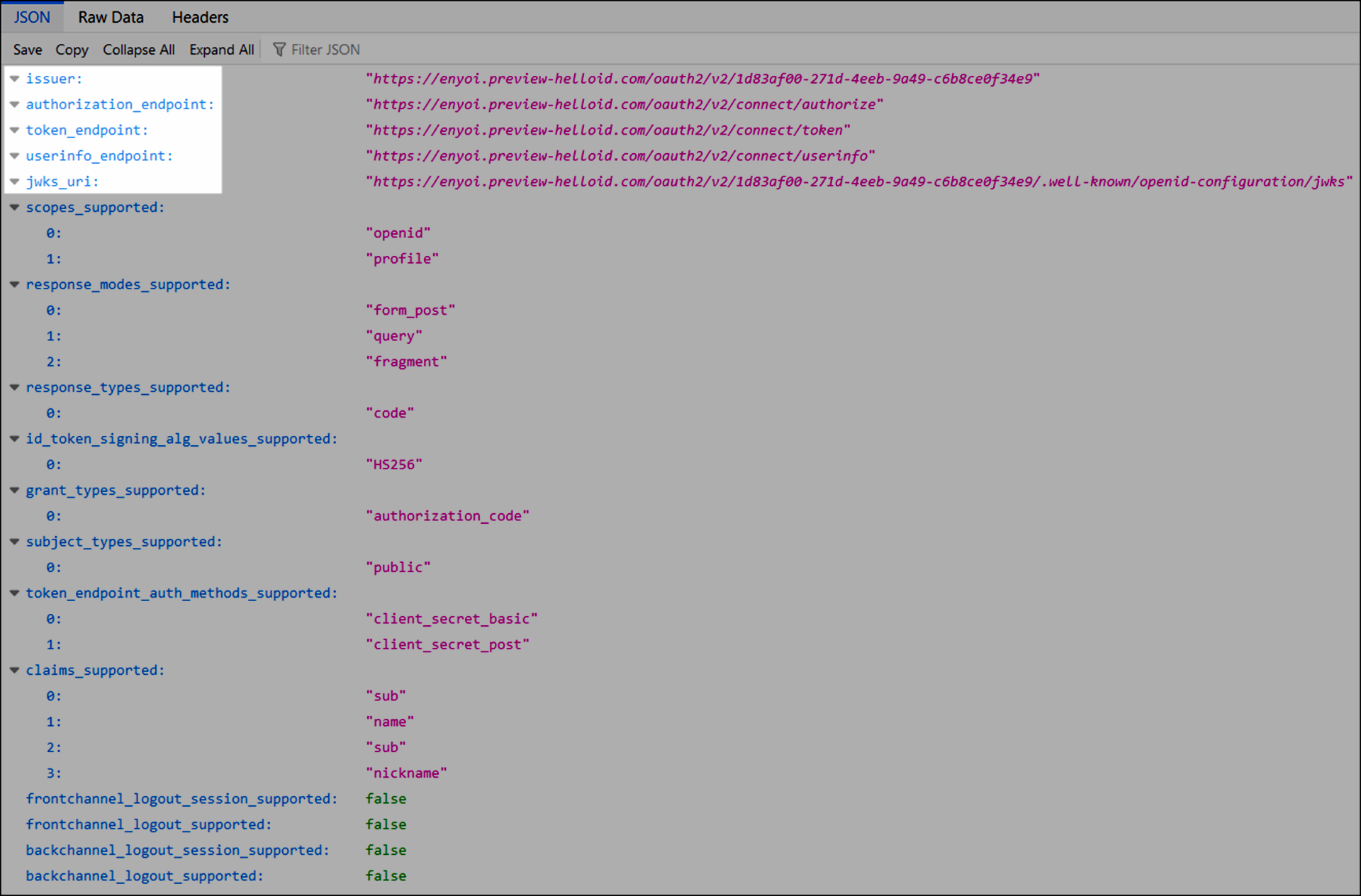
Enter the Authorize URI in the target app, in the format
https://<yourcustomerid>.helloid.com/oauth2/v2/connect/authorize.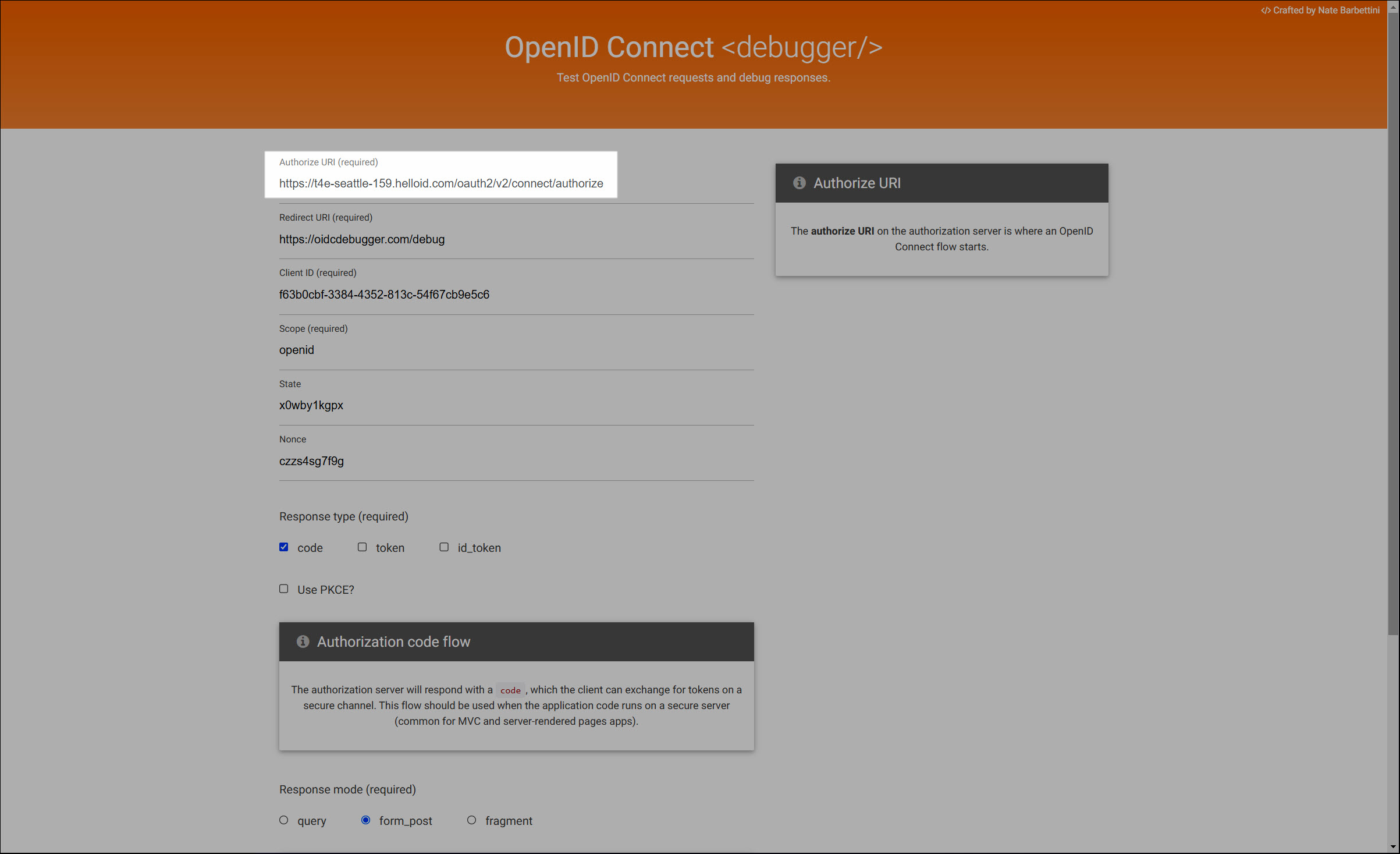
Tip
The Authorize URI can also be found in the
authorization_endpointfield in the app's discovery document, after saving the application.Copy the Redirect URI from the target app into the Redirect URI field in HelloID.
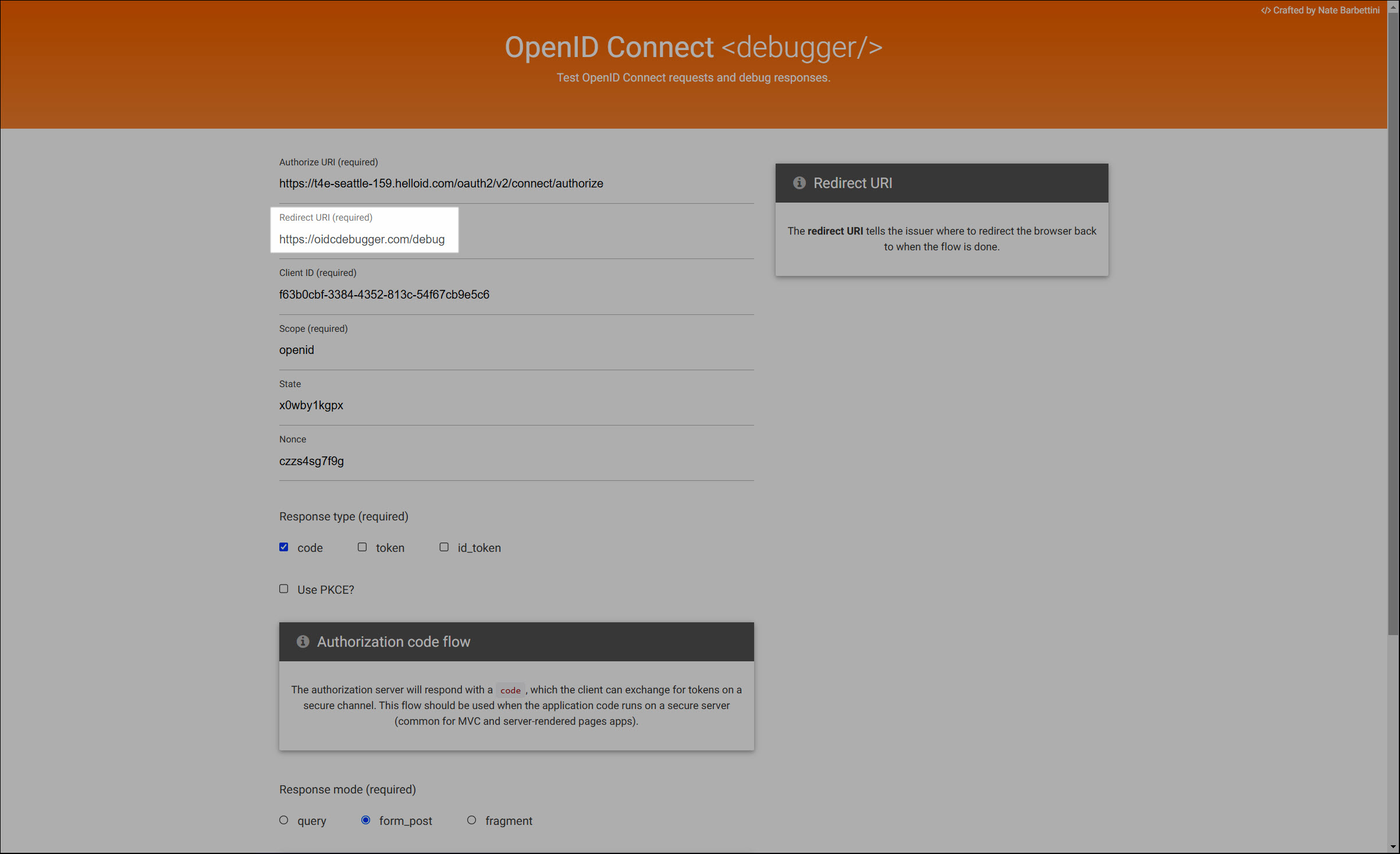
Click Next.
Optional: On the Self Service tab, enable the Generate Self Service Product toggle to automatically create a product (see Products) which grants access to this application. The Group is the group which will mediate access to the application (i.e., the group that the product will add the user to). If you select Generate Group, the name of the group will be
HelloIDApp.<AppName>.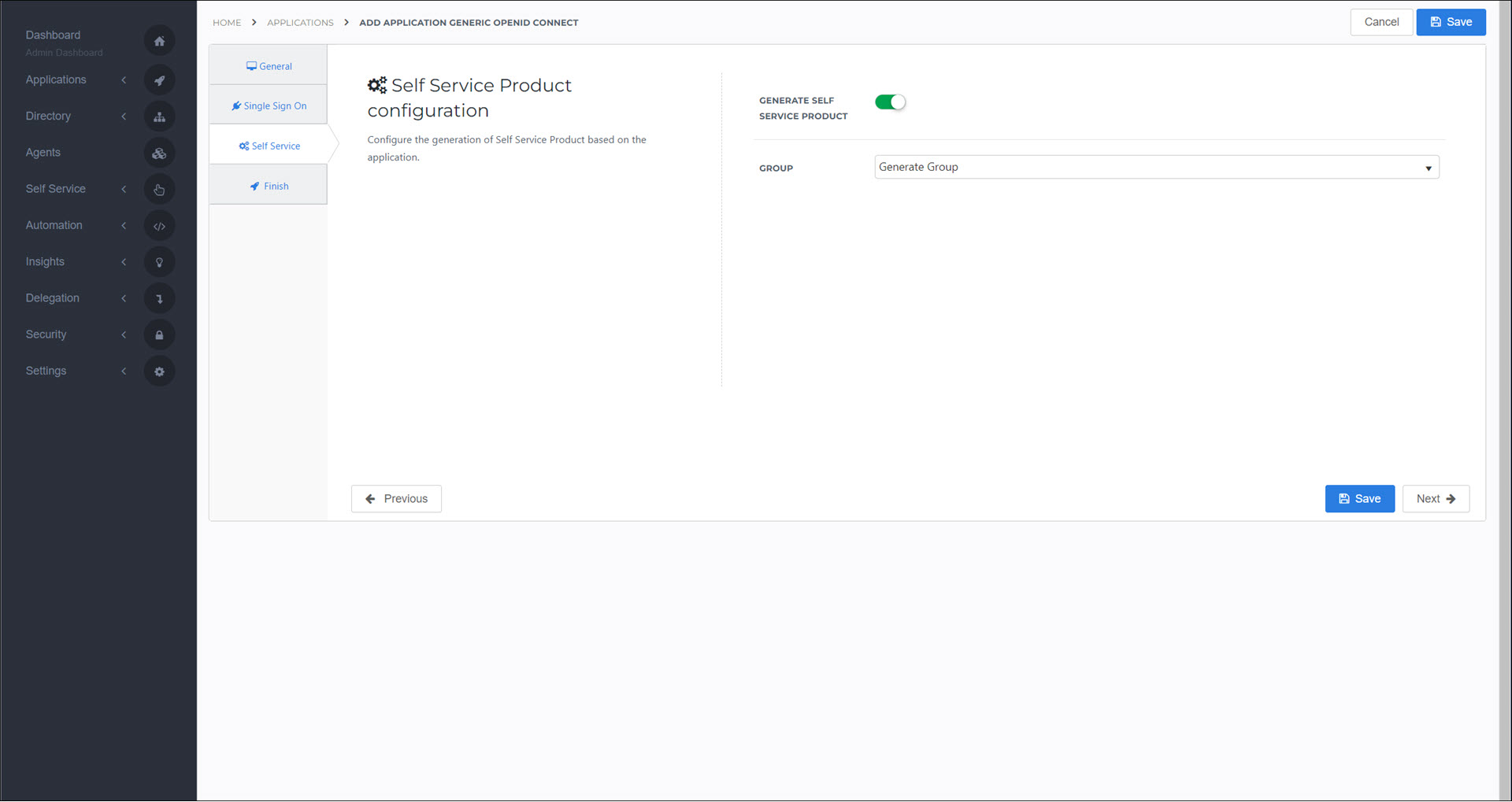
Click Next.
On the Finish tab, click Save.
The application has been created.
Optional: Grant a group access to an application to grant additional Groups access to this application.
Optional: Customize a mapping set for this application.
Optional:Add a product which grants access to an application
Optional: Configure Application access rules
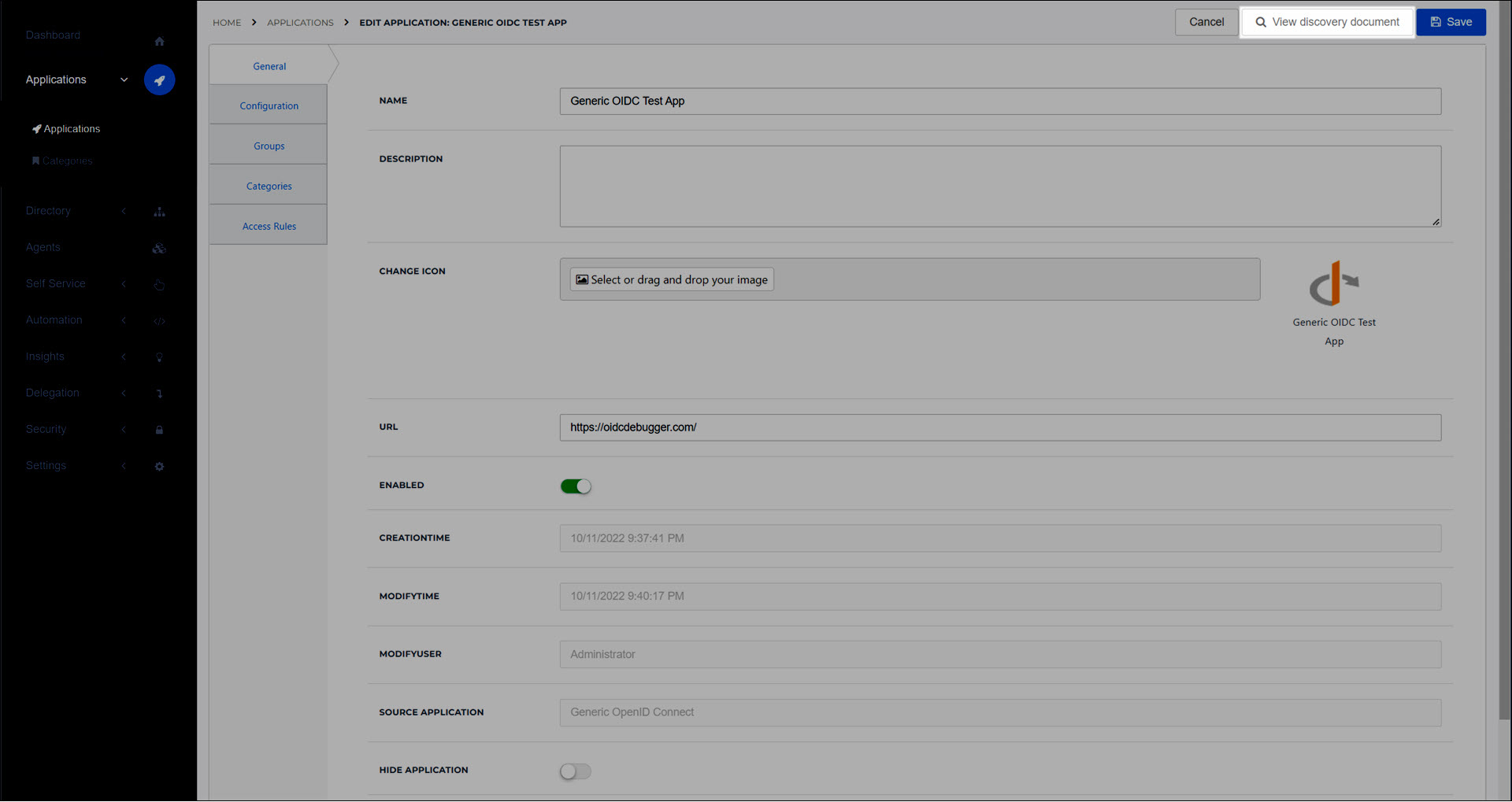
Depending on the client application, you may need to provide values from the discovery document.
The application is now available to users in the relevant groups, on the user dashboard (see Applications for users).

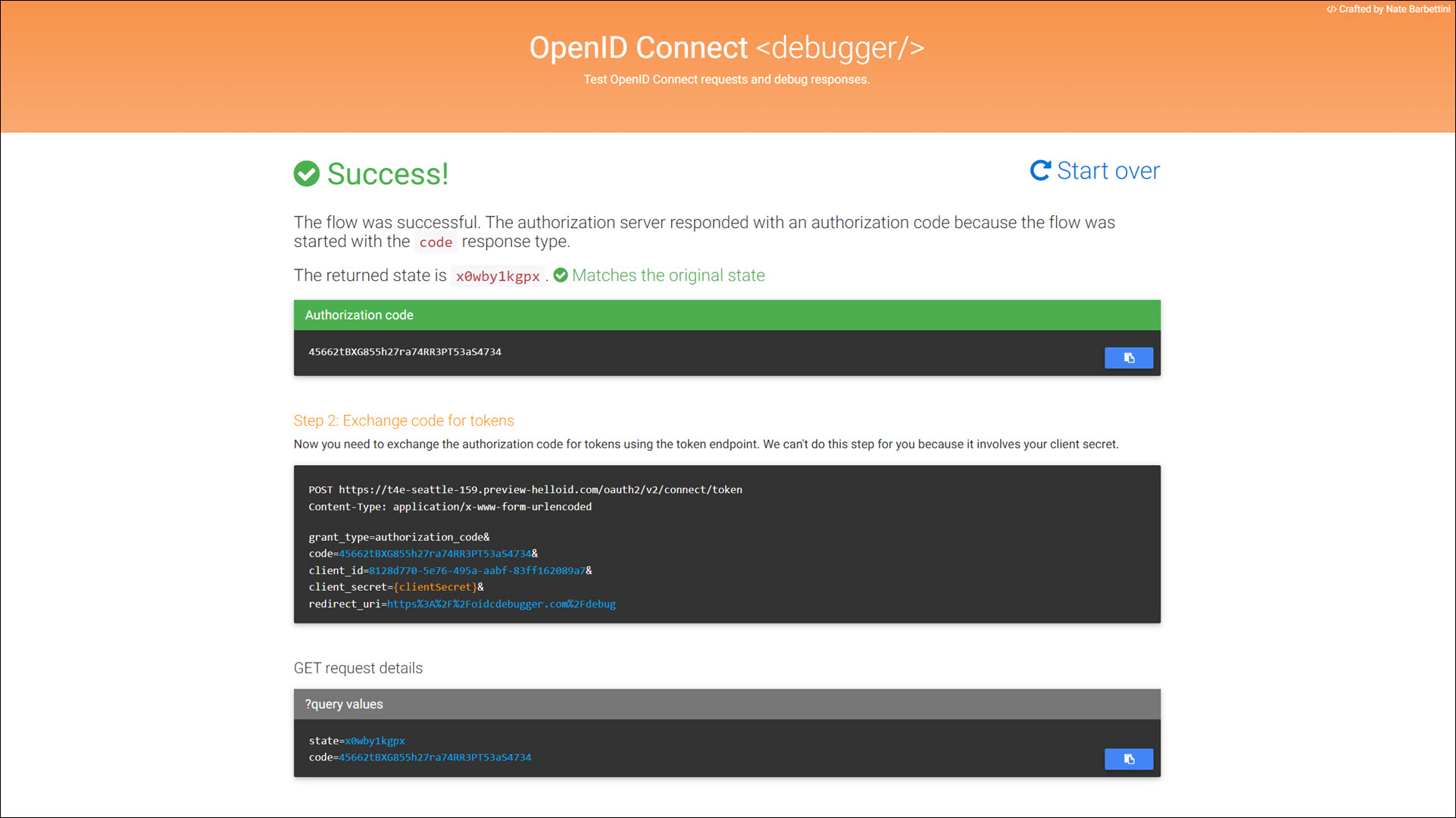
When you click the Send Request button in the OIDC debugger, it builds and sends a request. For example:
https://t4e-seattle-159.helloid.com/oauth2/v2/connect/authorize ?client_id=f63b0cbf-3384-4352-813c-54f67cb9e5c6 &redirect_uri=https%3A%2F%2Foidcdebugger.com%2Fdebug &scope=openid &response_type=code &response_mode=form_post &state=x0wby1kgpx &nonce=czzs4sg7f9g
You should get the following success screen: