Application settings reference
General tab (application settings)
- Name
The application's display name. Shown in the admin and user dashboards. Does not affect functionality.
- Description
The application's description. Shown in the admin and user dashboards. Does not affect functionality.
- Change Icon
The application's icon. Shown in the admin and user dashboards. Does not affect functionality.
- URL
The URL to launch when a user clicks this application on the user dashboard. Also known as the Default Login URL.
- Enable/Disable
Turn off to disable an application. Disabled applications cannot be launched by users, aren't displayed on the user dashboard, and do not handle incoming authentication requests. Compare to Hide Application.
- Creation Time
The date and time the application record was created. Read-only.
- Modify Time
The most recent date and time the application record was modified. Read-only.
- Modify User
The user who last modified the application record. Read-only.
- Source Application
The template in the App catalog which was used to create the application entry. Read-only.
- Hide Application
Hides the application in Applications for users. Unlike a disabled application, a hidden application still handles authentication requests from outside. Compare to Enable/Disable.
- Allow Show Credentials
Only has an effect for applications which use Application credentials. Let users View application credentials (see Credential sets) for this application. After you change this setting, a user must log out and back in for it to take effect.
When enabled, the values in the user's credential set will be prefilled in the text fields:
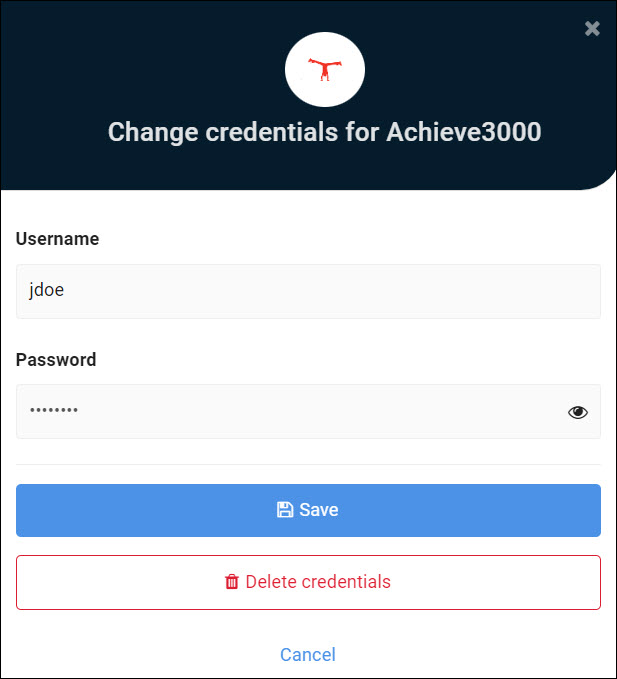
When disabled, the text fields are hidden:
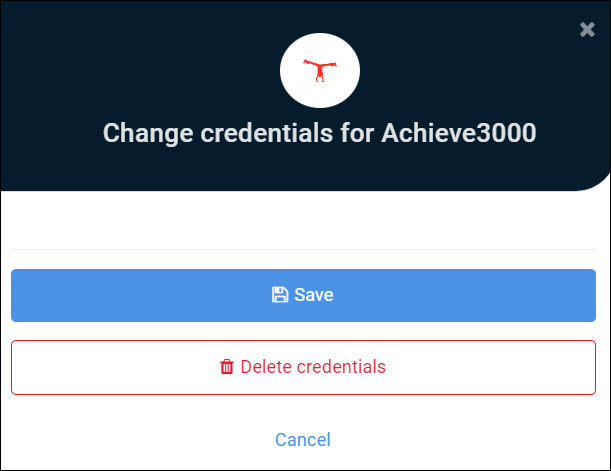
- Enable Change Password
Only has an effect for applications which use Application credentials. Lets users Update application credentials (see Credential sets) for this application. After you change this setting, a user must log out and back in for it to take effect.
Typically, when you enable this setting, you'll also want to enable Allow Show Credentials.
For example, here this setting is enabled for the Achieve3000 application, allowing the user to edit their credential set for it:
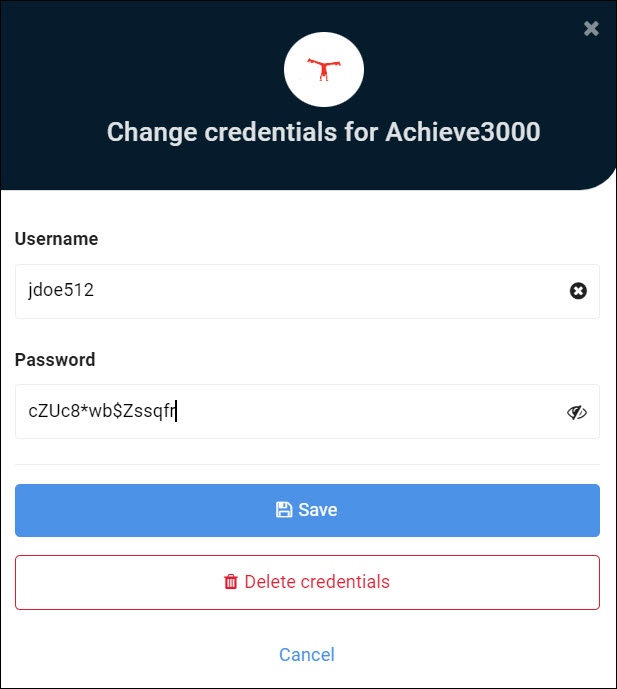
Important
This setting only has an effect when the application's credential source is set to Credentials Are Entered By User, or to Credentials Are Configured By Admin and at least one field is set to User Enters .... For fixed, non user-editable credential sources, this setting has no effect even when enabled.
Configuration tab (SAML application settings)
- Name ID Format
Required. The format of the unique identifier expected by the SP.
persistenttransientemailaddressunspecified
- Issuer
Optional. The unique identifier (entityID) HelloID in SAML responses. Generally set to your HelloID base URL:
http://<yourcustomerid>.helloid.com, which is the default if no value is entered.- Endpoint/ACS URL
Required. The Assertion Consumer Service (ACS) endpoint where the SP will receive SAML assertions issued by HelloID. Obtained from the
Locationproperty of themd:AssertionConsumerServicetag in the SP metadata.- Validate And Use ACS Request URL
Optional, but should be enabled for security reasons if possible. Enables validation of the AuthnRequest
AssertionConsumerServiceURLattribute.- ACS Validation List
If Validate And Use ACS Request URL is enabled, enter the list of values here.
- Binding
Required. The method used to send the request. Depends on the
md:AssertionConsumerServicetag of theBindingproperty in the SP metadata.HTTP-PostHTTP-Redirect
- SP-Initiated URL
Optional. For SPs that require SP-initiated requests. If there are multiple SP-initiated URLs, use Application shortcuts.
- RelayState
Optional. Identifies the specific resource that the user will access after they are signed in and directed to the relaying party's federation server.
- Sign Assertion
Sign the assertion using the X509 Certificate.
- X509 Certificate
Required. The certificate used to sign the request if Sign Assertion is enabled.
- Sign Response
Sign the response.
- Use DS Prefix
Add additional SAML prefixing to the assertion. Only enable if required.
- Encrypt Assertion
Encrypt the assertion using the X509 Encryption Certificate.
- X509 Encryption Certificate
The certificate used to encrypt the assertion. Typically provided by the SP in the
"ds:X509Certicate"tag in the SP metadata. You will need to import this certificate into HelloID before you can select it. See Import a certificate.- Use Custom Digest And Signature Methods
Use a custom digest and signature method to sign the response. If disabled, SHA256 will be used.
- Custom Digest Method
The custom digest method to use, if Use Custom Digest And Signature Methods is enabled.
- Custom Signature Method
The custom signature method to use, if Use Custom Digest And Signature Methods is enabled.
- Send Group Membership Attribute
Send a list of group memberships inside the attribute statement of the assertion.
- Group Membership Attribute Name
The
Nameof the attribute containing membership information (e.g.,memberOf)- Overwrite Audience
Specified by the SP. Allows enforcement of only the audiences specified in the the Extra Audience field.
- Extra Audience
A comma-separated list of audience values. Only used when Overwrite Audience is enabled. Can be found in the
md:AssertionConsumerServicetag in the metadata XML provided by the SP.- Mapping Set
The application mapping set used to build the SAML claim set. See Application mapping sets.
- Download Metadata
Download the application's XML metadata, to provide to the SP.
Configuration tab (OIDC application settings)
- Client ID
Used for application-side configuration.
- Secret
A shared value between HelloID and the application. The secret will be automatically generated but can be changed if needed. A custom secret should have a minimum length of 10 characters.
- Security Algorithm
Depends on the required settings for the client application and the desired connection method.
- Signing Certificate
Used to verify the token. The token will need to be identical on both the client and the server side of the connection.
- Grant Type
Depends on the required settings for the client application and the desired connection method.
- Supported Scopes
The scopes enabled for this application.
- Redirect URI
The redirect URI configured in the client app must match one of the values entered in this field. This is useful, for example, to run production and test environments at the same time. You may enter multiple redirect URIs by pressing Enter on your keyboard after typing a value.
- Mapping Set GUID
The GUID for the mapping set associated with this application.
- Send Group Membership Claim
Include HelloID group memberships of the requesting user in the generated token.
- Group Membership Claim Name
The label that will be applied to the group membership claim section in the token. This value is chosen by the OpenID application provider.
- Refresh Token Lifetime In Days
The number of days the refresh token should remain valid.