Templafy SAML application setup
Introduction
This article demonstrates how to set up Templafy for single sign-on. The configuration takes place in HelloID and requires you to send information to Templafy.
Requirements
HelloID environment
Templafy environment
Create or import a certificate
If there is no certificate yet, you must create or import one. For this tutorial, we will create a self-signed certificate.
Application setup
Add the Templafy application
Add a new application.
Find the template for Templafy
Select its Add button.
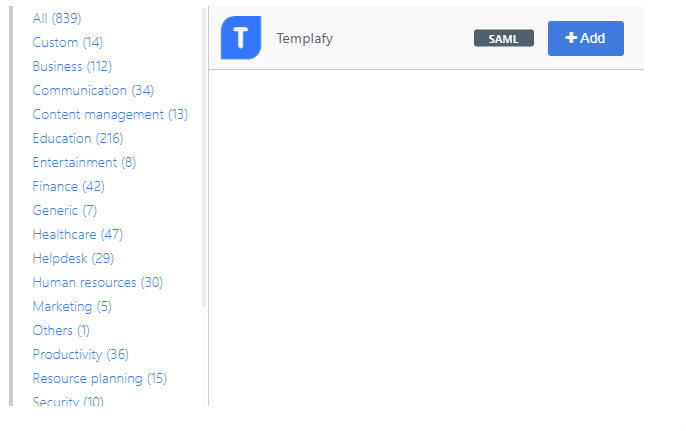
General tab
Change the following settings:
Default Login URL
Enter your Templafy environment URL. For example:
https://{customer}.templafy.com.
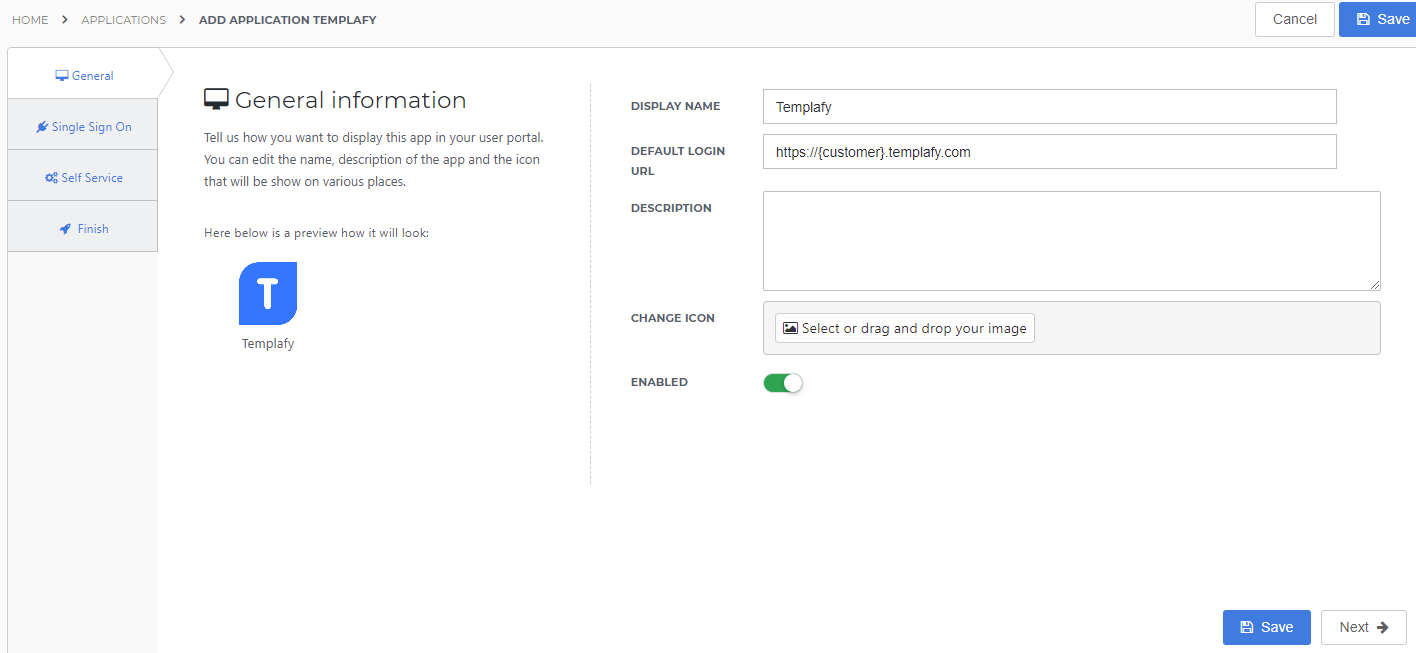
Select the Next button.
Single Sign-On tab
Change the following settings:
Endpoint URL
Enter your Templafy ACS environment URL in the format
https://{custom}.auth.templafy.com/auth/saml2/auth-services/Acs. This URL can be obtained from Templafy or found in the Templafy metadata file. This URL is case sensitive.ACS validation listEnter the same value you entered for the Endpoint URL.
X509 CertificateSelect the certificate that you previously imported or created.
SP-Initiated URLEnter your Templafy environment URL. For example:
https://{customer}.templafy.com.Send group membership attributeTurn on this toggle to send the group memberships of the user to Templafy.

Select the Next button.
Self Service tab
Optionally, generate a Self Service product, which makes the application requestable. Select a group which will have access to the product.
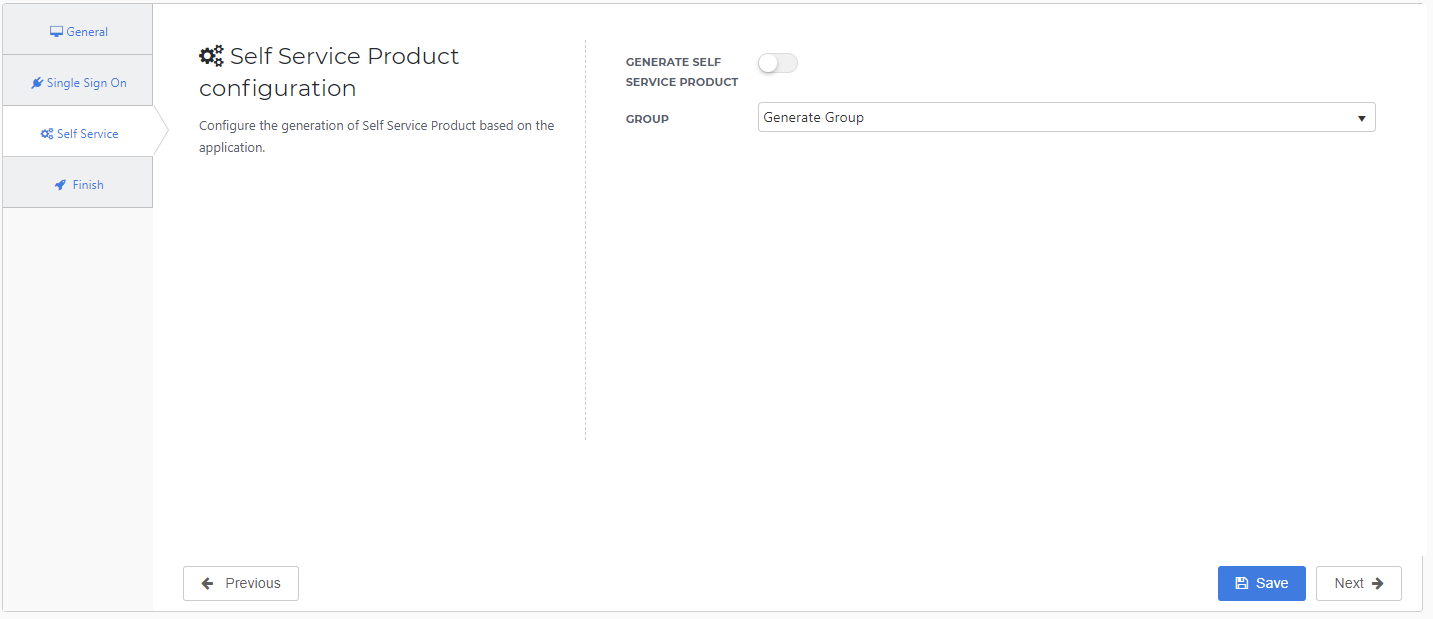
Select the Next button.
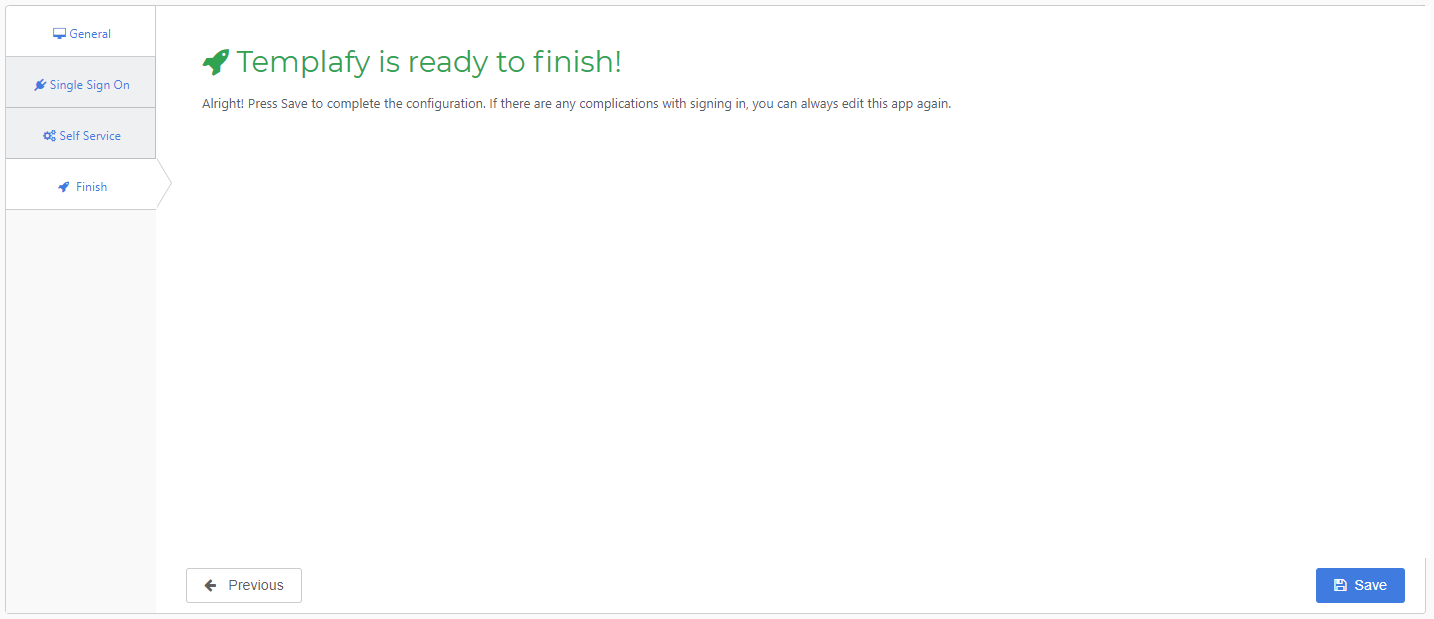
Finish tab
Select the Save button to add the Templafy application to HelloID.
Additional configuration
Mapping
By default, the user's HelloID {{user.contactEmail}} attribute is sent as the SAML NameID.
The following attributes are sent by default:
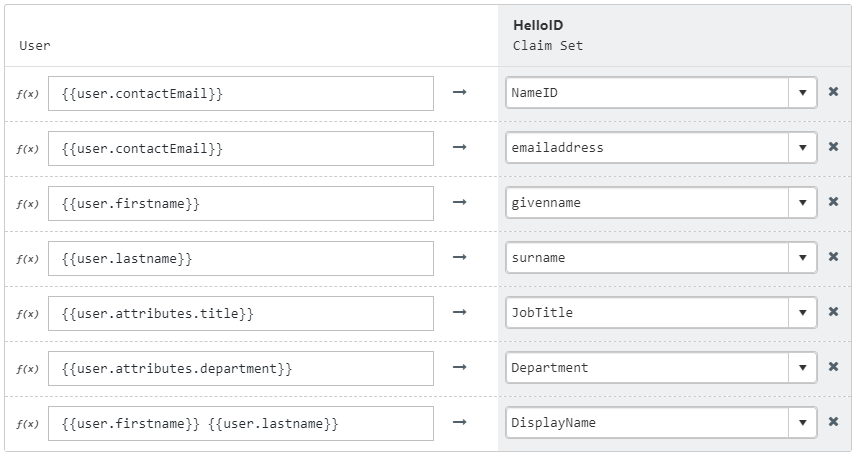
If you wish to change the mapping see Mapping - Overview.
The default attributes include all those which Templafy currently supports. If you change them, you must communicate this to Templafy. For more information see: https://support.templafy.com/hc/en-us/articles/207724789-Supported-claims-and-claims-rules
Supplier-side configuration
The HelloID side of the configuration is now finished.
To connect, Templafy needs to add the connection on their side. Contact Templafy to request this.
Send them the following information:
Metadata URL
Metadata URL
Go to the Applications overview.
Select the Edit link for the newly-added Templafy application.
Right-click the Download metadata button
Select Copy link address. It will resemble:
https://enyoi.helloid.com/metadata/download?ApplicationGUID=e6e741f5-a469-4849-93f7-fe2e259a339f.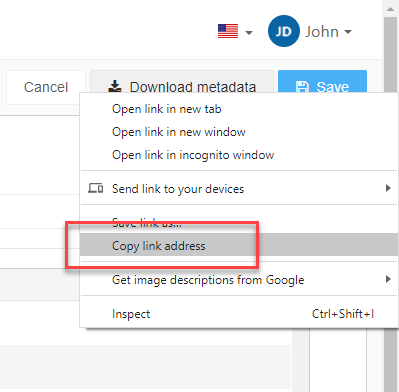
Finish up
The Templafy application has been added to HelloID, and a trust has been configured between Templafy and HelloID. You are now free to test the application and assign it to users within your organization. See Applications - Overview and its related articles for more information.