Security (Azure AD target systems)
The connector for Azure AD target systems uses the Microsoft Graph API to provision users and group memberships. It connects using Azure's Admin Consent feature, which grants access via an OpenID Connect flow. The application secret and application ID are stored encrypted in HelloID and cannot be seen or retrieved.
By default, HelloID requests the following permissions:
Read and write all users' full profiles
Read and write all groups
Read directory data
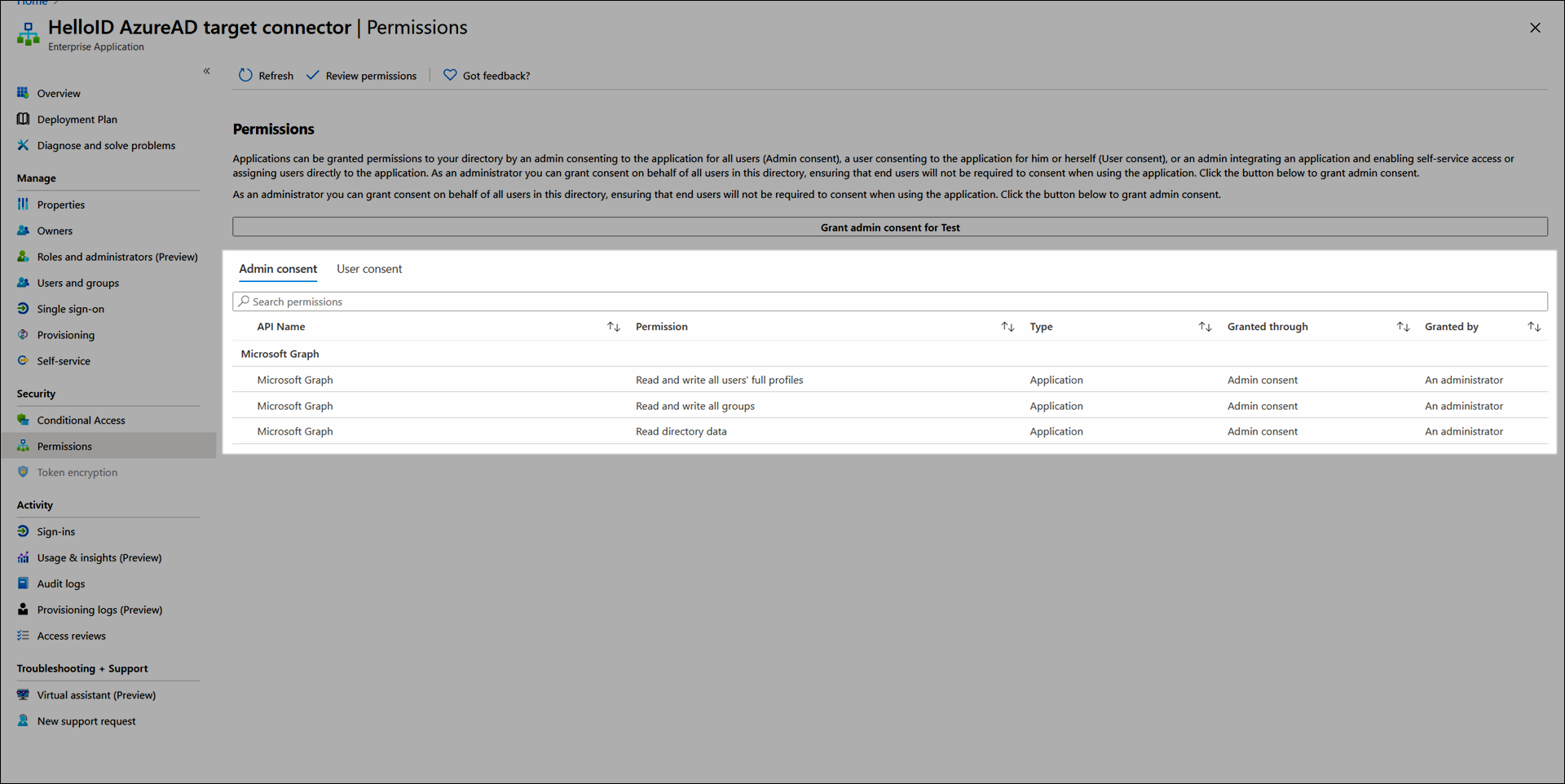
If needed, you can change these permissions in the Azure portal. To do so:
Select the Azure Active Directory button.
Select the Enterprise Applications link.
Select the HelloID Azure AD Target Connector link.
Select the Permissions link.
Note that removing existing permissions may lead to errors in the provisioning process.
All actions performed by HelloID are listed under the Azure enterprise application's Audit Logs section.