Microsoft RDWeb via WS-Federation application setup
Introduction
You can use HelloID as an Identity Provider (IdP) for Microsoft RDWeb, using WS-Federation (Web Services Federation).
This configuration requires communication with Tools4ever support.
Requirements
HelloID environment
RDWeb 2016 or 2019 environment with full administrative rights
Create or import a certificate
Create or import a self-signed certificate named
RDWeb.Download the certificate as a DER Encoded binary X.509 (.CER) file.
Save the .CER file to the RDWeb server and make note of its location. You will need it shortly.
Download the certificate as a Personal Information Exchange (.PFX) file.
Supply it to Tools4ever support. Tools4ever will convert the .PFX certificate into a format compatible with the RDWeb server, and send you a copy.
When you receive the converted certificate, import it into HelloID. Name it
RDWeb WS-Federation. Ignore any certificate errors.
Application setup
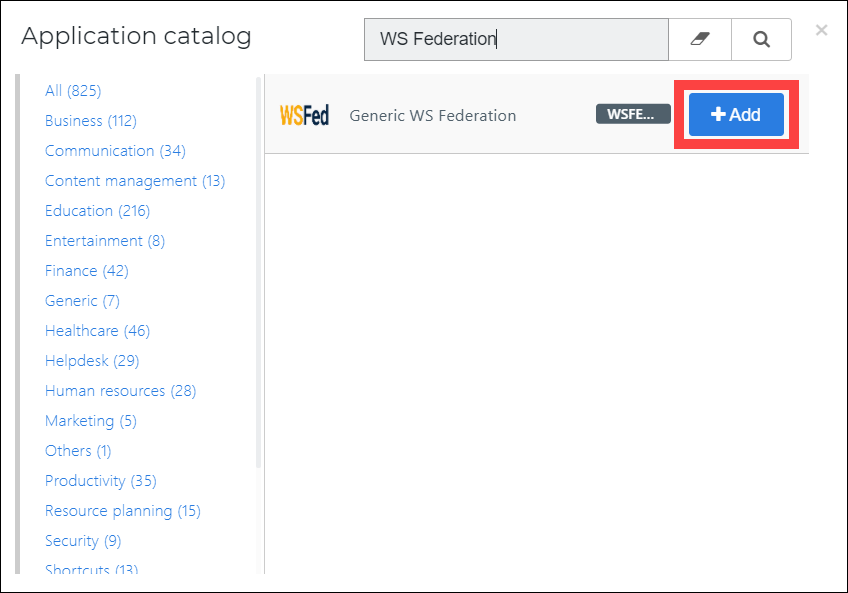
Open the HelloID application catalog.
Add the Generic WS Federation application.
General tab
For the Default Login URL, enter your RDWeb URL. For example:
https://remote.customer.com/RDWeb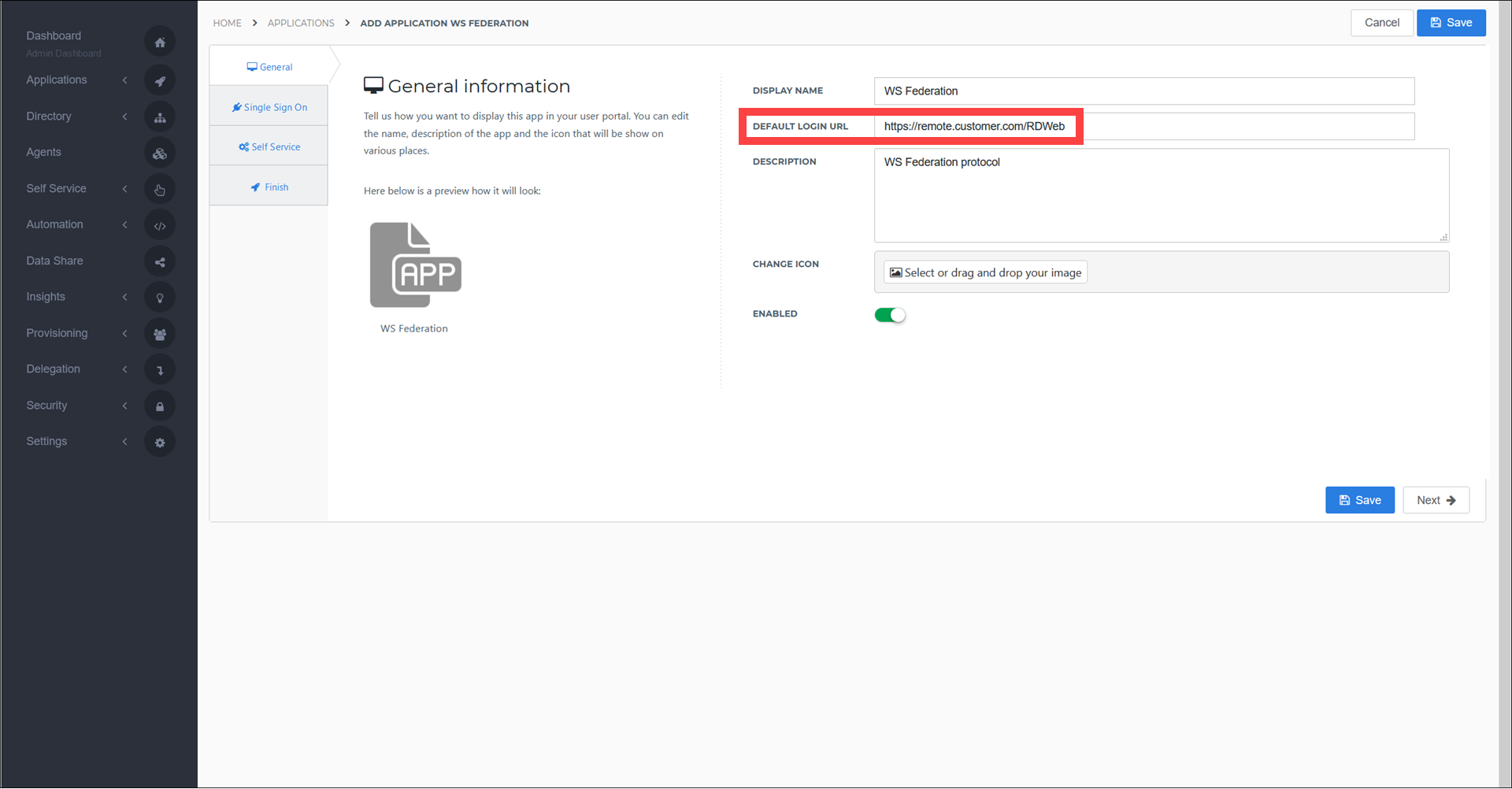
Single Sign On tab
For the Realm field, enter the RDWeb URL with the addition of
/Pages/. For example:https://remote.customer.com/RDWeb/Pages/.For the Endpoint URL field, enter the RDWeb URL with the addition of
/Pages. For example:https://remote.customer.com/RDWeb/Pages.For the X509 Certificate field, select the RDWeb WS-Federation certificate you received from Tools4ever support.
Save the application.
Change mappings
Edit the mapping set of the new WS Federation application.
Select the Change mappings link.
Remove all existing mappings.
Add a mapping for
{{user.contactEmail}} > Upn.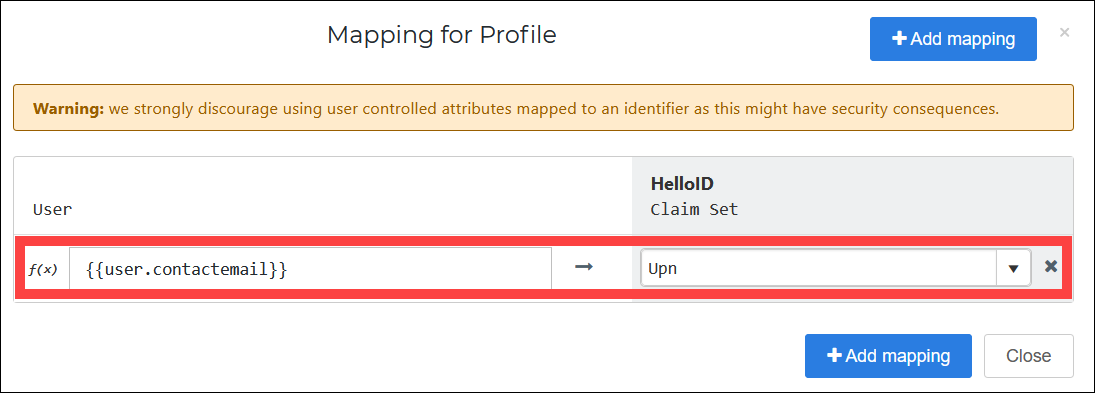
Add additional custom mappings as desired.
Select the Set Identifier link.
Remove the existing mapping.
Add a mapping for
{{user.contactEmail}} > Name ID.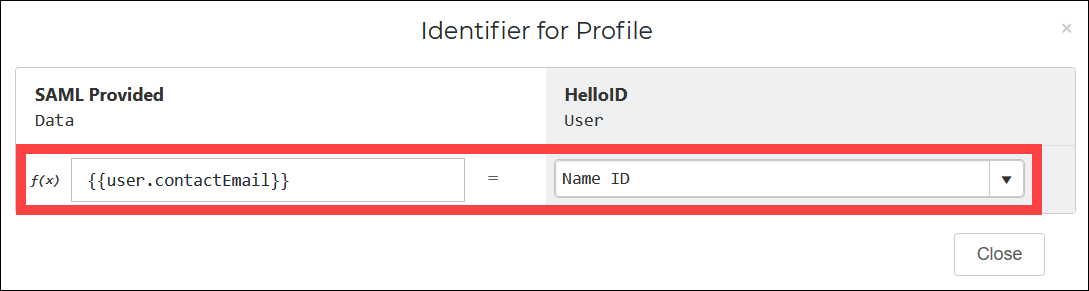
Select the Close link, and then select the Save button.
RDWeb server configuration
Install the certificate you previously copied to the RDWeb server.
Open the Certificates snap-in.
Double-click the added certificate.
Select the Details tab.
Select the Thumbprint field and copy its hex value.
Install Windows Identity Foundation using the Server Manager Roles and Features Wizard.
Open Notepad.exe as administrator. Open the file:
C:\Program Files\Windows Identity Federation\v3.5\c2wtshost.exe.config. Create a backup if desired.Add
<add value= "IIS APPPOOL\RDWebAccess" />above the</allowedCallers>line. The result should look like this:<allowedCallers> <clear/> <!-- <add value="NT AUTHORITY\Network Service" /> --> <!-- <add value="NT AUTHORITY\Local Service" /> --> <!-- <add value="NT AUTHORITY\System" /> --> <!-- <add value="NT AUTHORITY\Authenticated Users" /> --> <add value= "IIS APPPOOL\RDWebAccess" /> </allowedCallers>
Open the Services snap-in.
Start the Claims to Windows Token Service.
Set its Startup Type to Automatic.
Ensure that it depends on the Cryptographic Service by running the following command as administrator:
sc config c2wts depend= cryptsvcOpen the IIS Manager.
Browse to the RDWebAccess Application Pool.
Select Advanced Settings.
Set Load User Profile to
True.Select OK.
Recycle the application pool.
Open Notepad.exe as administrator. Open the file:
C:\Windows\Web\RDWeb\Pages\web.config. Create a backup if desired.Add the following directly under the
<configuration>tag:<configSections> <section name= "microsoft.identityModel" type= "Microsoft.IdentityModel.Configuration.MicrosoftIdentityModelSection, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" /> </configSections>
The result should look like this:
<configuration> <configSections> <section name= "microsoft.identityModel" type= "Microsoft.IdentityModel.Configuration.MicrosoftIdentityModelSection, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" /> </configSections> <!-- Admin Defined settings -->
Add the following lines directly under the
<system.web>tag:<httpRuntime requestValidationMode= "2.0" /> <pages validateRequest= "false" />
Add the following lines inside the
<system.web>tag:<authorization><deny users= "?" /></authorization> <authentication mode= "None" />
Disable all other authentication methods by commenting them out using
<!-- -->.<!-- <authentication mode="Forms"> <forms loginUrl="default.aspx" name="TSWAAuthHttpOnlyCookie" protection="All" requireSSL="true" /> </authentication> -->
Change the runAllManagedModulesForAllRequests setting to
True.Add the following two lines directly above the
</modules>tag:<add name= "WSFederationAuthenticationModule" type= "Microsoft.IdentityModel.Web.WSFederationAuthenticationModule, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" preCondition= "managedHandler" /> <add name= "SessionAuthenticationModule" type= "Microsoft.IdentityModel.Web.SessionAuthenticationModule, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" preCondition= "managedHandler" />
Edit the following lines inside the
<runtime>tag:<microsoft.identityModel> <service> <audienceUris> <add value= "urn:microsoft:rdweb" /> <add value= "https://rdweburl/RDWeb/Pages/"/> </audienceUris> <securityTokenHandlers> <remove type= "Microsoft.IdentityModel.Tokens.SessionSecurityTokenHandler, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" /> <add type= "Microsoft.IdentityModel.Tokens.SessionSecurityTokenHandler, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" > <sessionTokenRequirement useWindowsTokenService= "true" /> </add> <add type= "Microsoft.IdentityModel.Tokens.Saml11.Saml11SecurityTokenHandler, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" > <samlSecurityTokenRequirement mapToWindows= "true" useWindowsTokenService= "true" /> </add> </securityTokenHandlers> <federatedAuthentication> <wsFederation passiveRedirectEnabled= "true" issuer= "https://we-identity.helloid.cloud/service/identity-server/wsfederation/suppliedbytools4ever" realm= " https://rdweburl/RDWeb/Pages/" " requireHttps= "true" /> <cookieHandler requireSsl= "false" /> </federatedAuthentication> <applicationService> </applicationService> <issuerNameRegistry type= "Microsoft.IdentityModel.Tokens.ConfigurationBasedIssuerNameRegistry, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" > <trustedIssuers> <add thumbprint= "Certificate thumbprint copied earlier" name= "Name of the certificate authority" /> </trustedIssuers> </issuerNameRegistry> <certificateValidation certificateValidationMode= "None" /> </service> </microsoft.identityModel>
Save the
web.configfile.Test the authentication, starting with the RDWeb server. Note the trailing
/in the URL. If you receive errors about duplicate entries in theweb.configfile, comment out the duplicate lines and try again.