Provisioning audit log reports
This report space contains Audit log reports for HelloID's Provisioning module.
Entitlement actions (audit log reports)
Entitlement Actions - Successful Overview (audit log report)
Shows recent successful entitlement actions in Target systems (including Grant, Revoke, and Update actions).
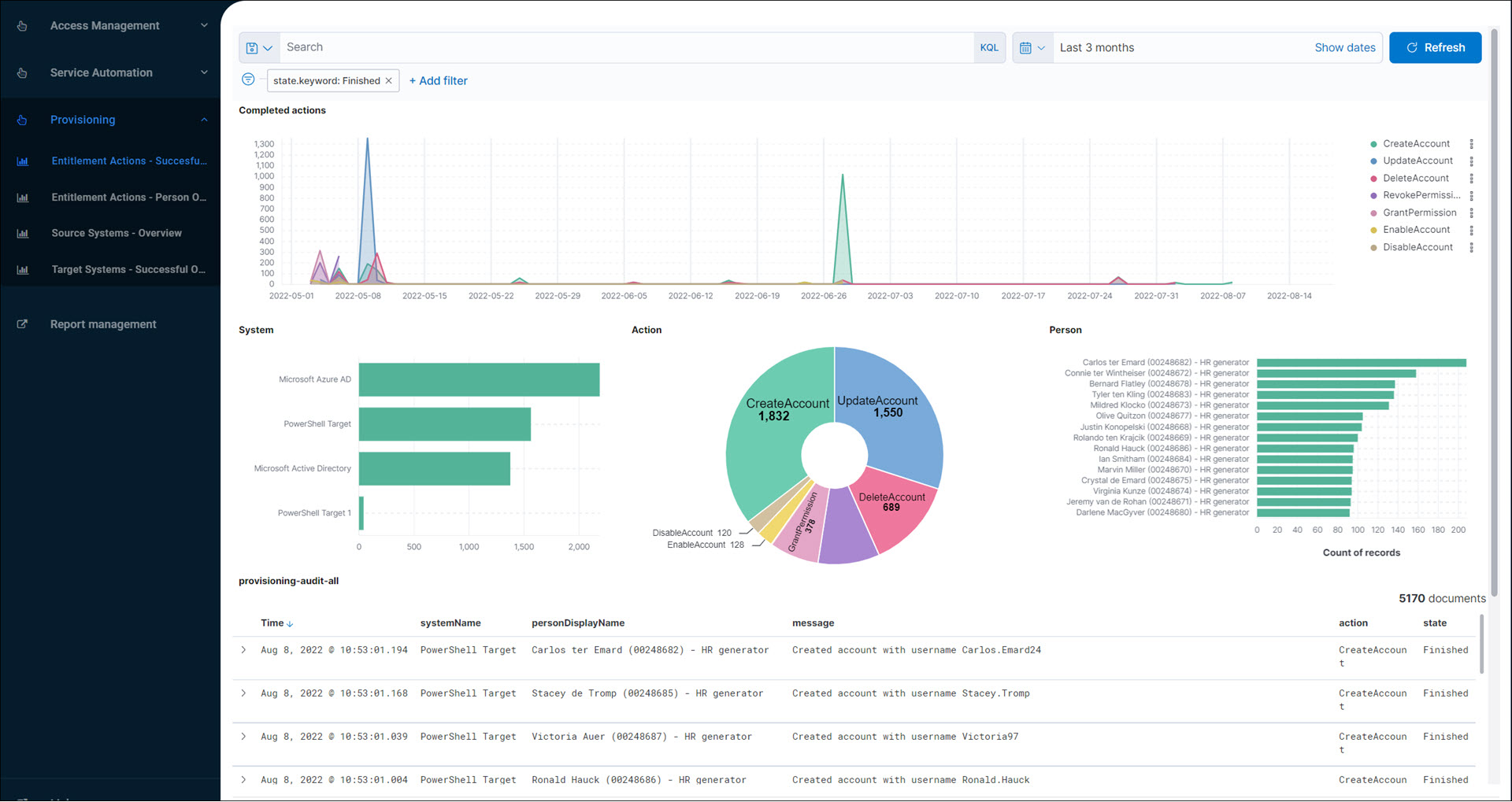
Entitlement Actions - Person Overview (audit log report)
Shows recent entitlement actions by by person. This is the same data shown when you View a person's audit logs.
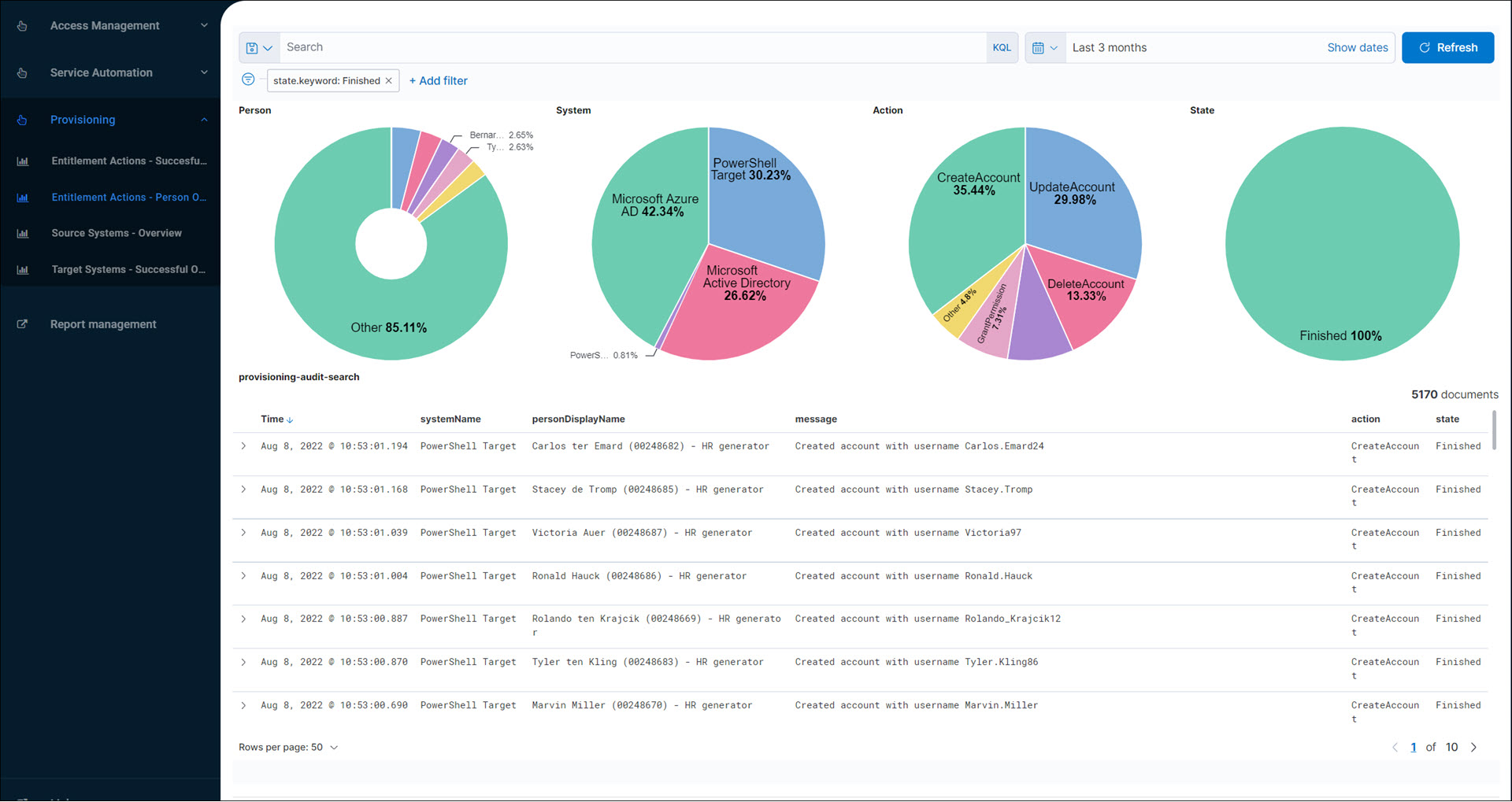
Source systems (audit log reports)
Source Systems - Overview (audit log report)
Shows recent Source snapshots in Source systems.
Target systems (audit log reports)
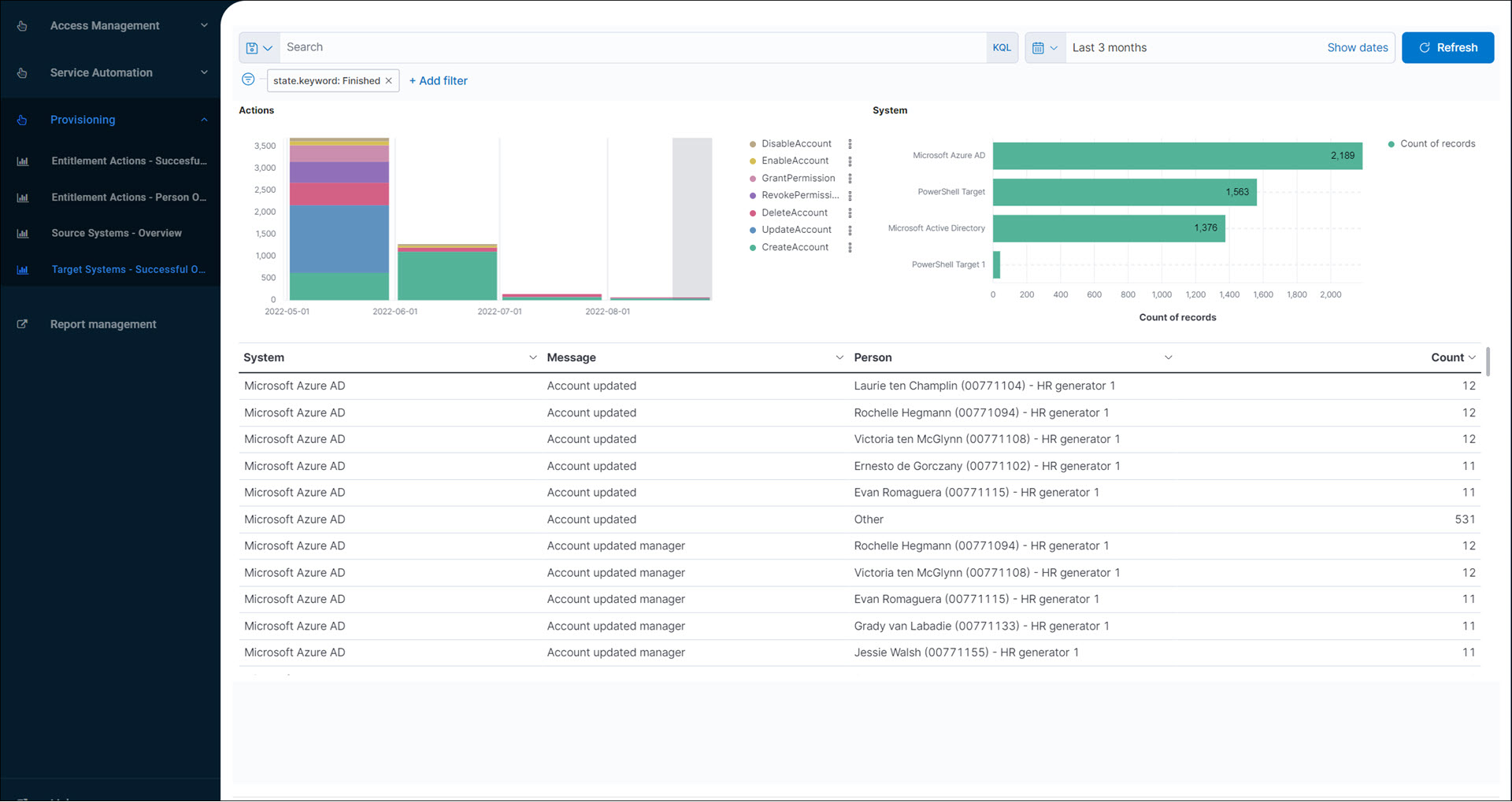
Target Systems - Successful Overview (audit log report)
Shows recent successful entitlement actions in Target systems (including Grant, Revoke, and Update actions), with a focus on disaggregation by target system.
Business Rules (audit log reports)
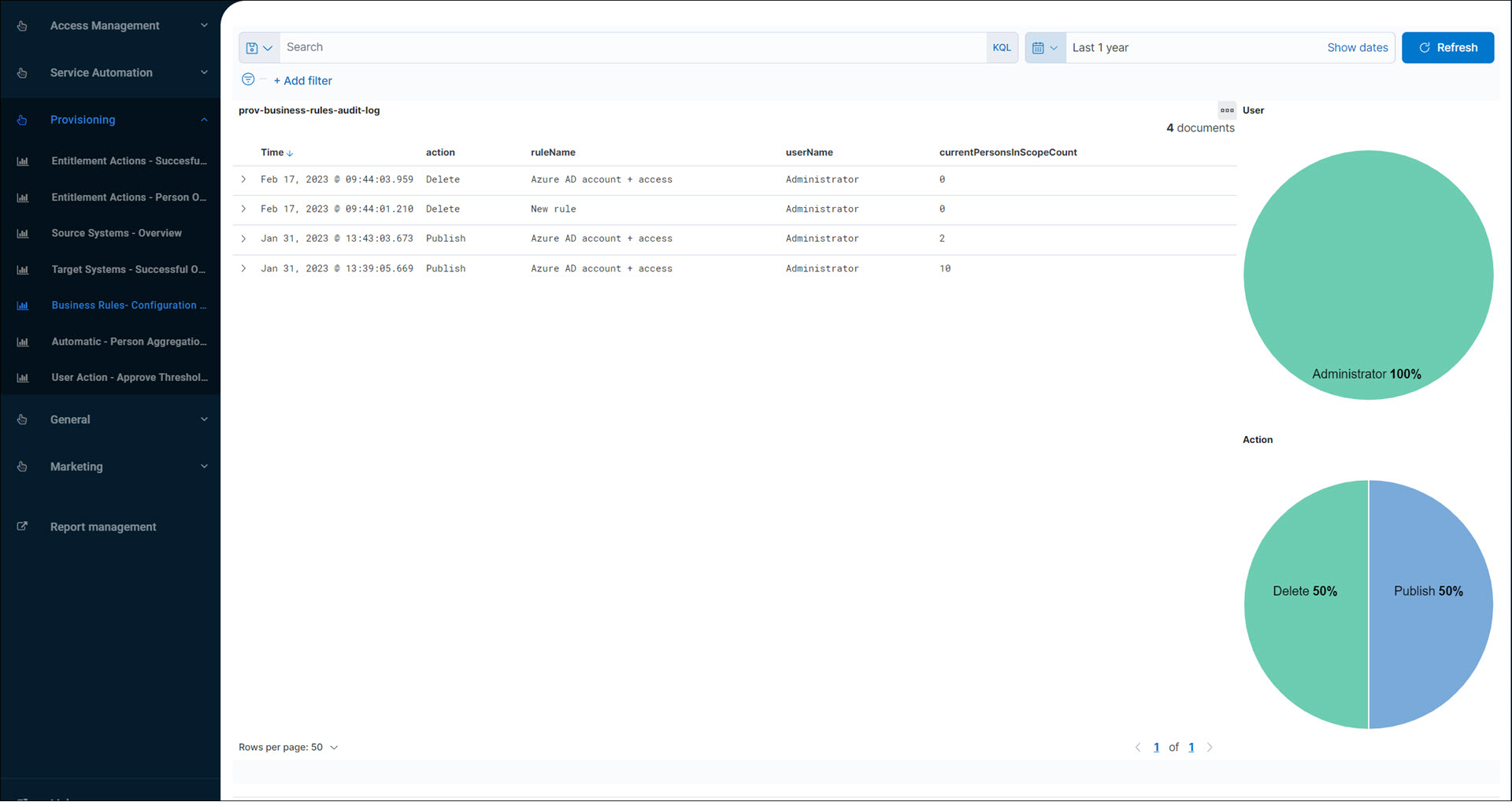
Business Rules - Configuration Changes (audit log report)
Shows recent changes to Business rules, including the user who made the change.
Person Aggregation (audit log reports)
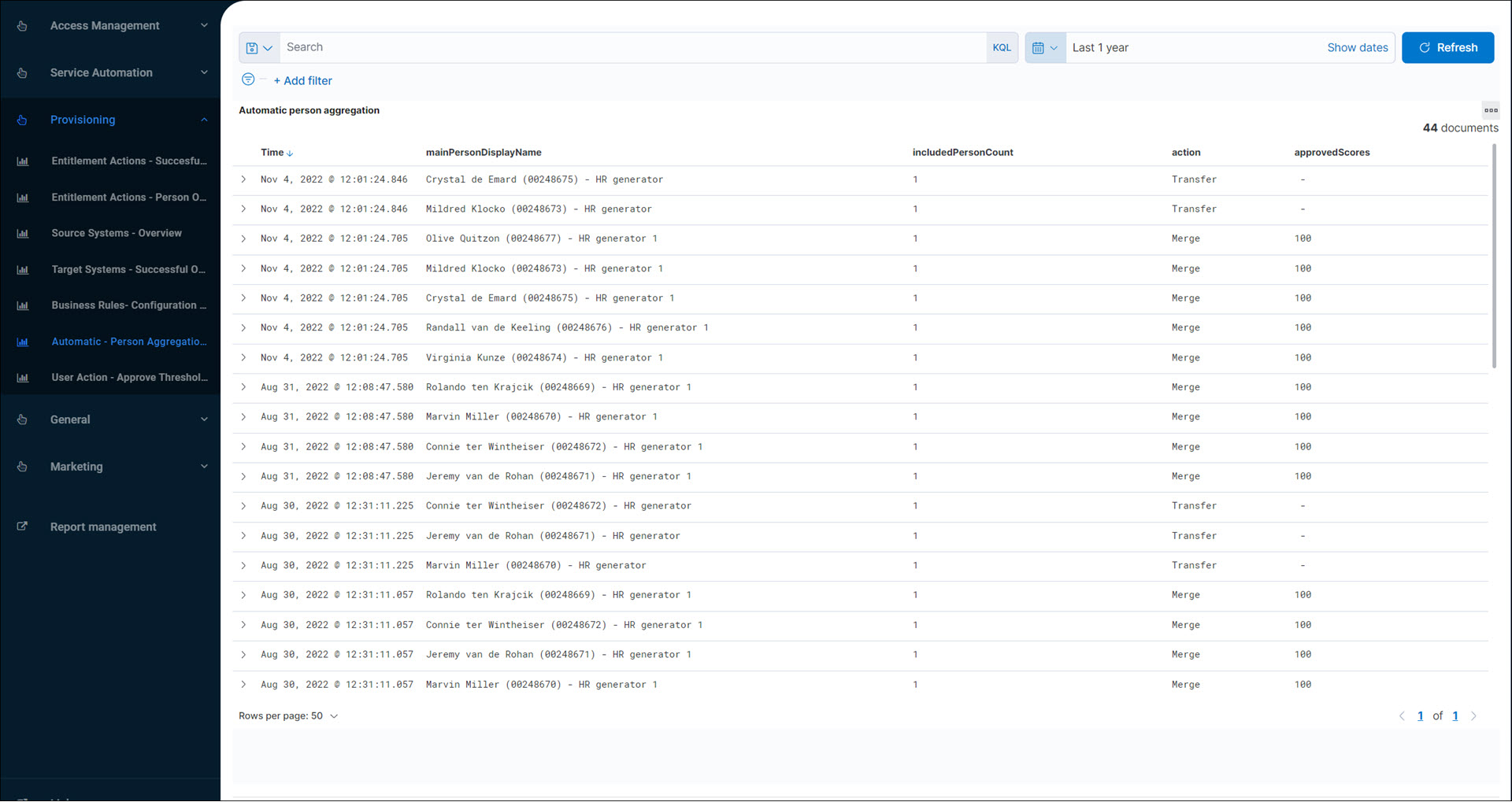
Automatic - Person Aggregation Overview (audit log report)
Shows recent Person aggregation actions.
User Actions (audit log reports)
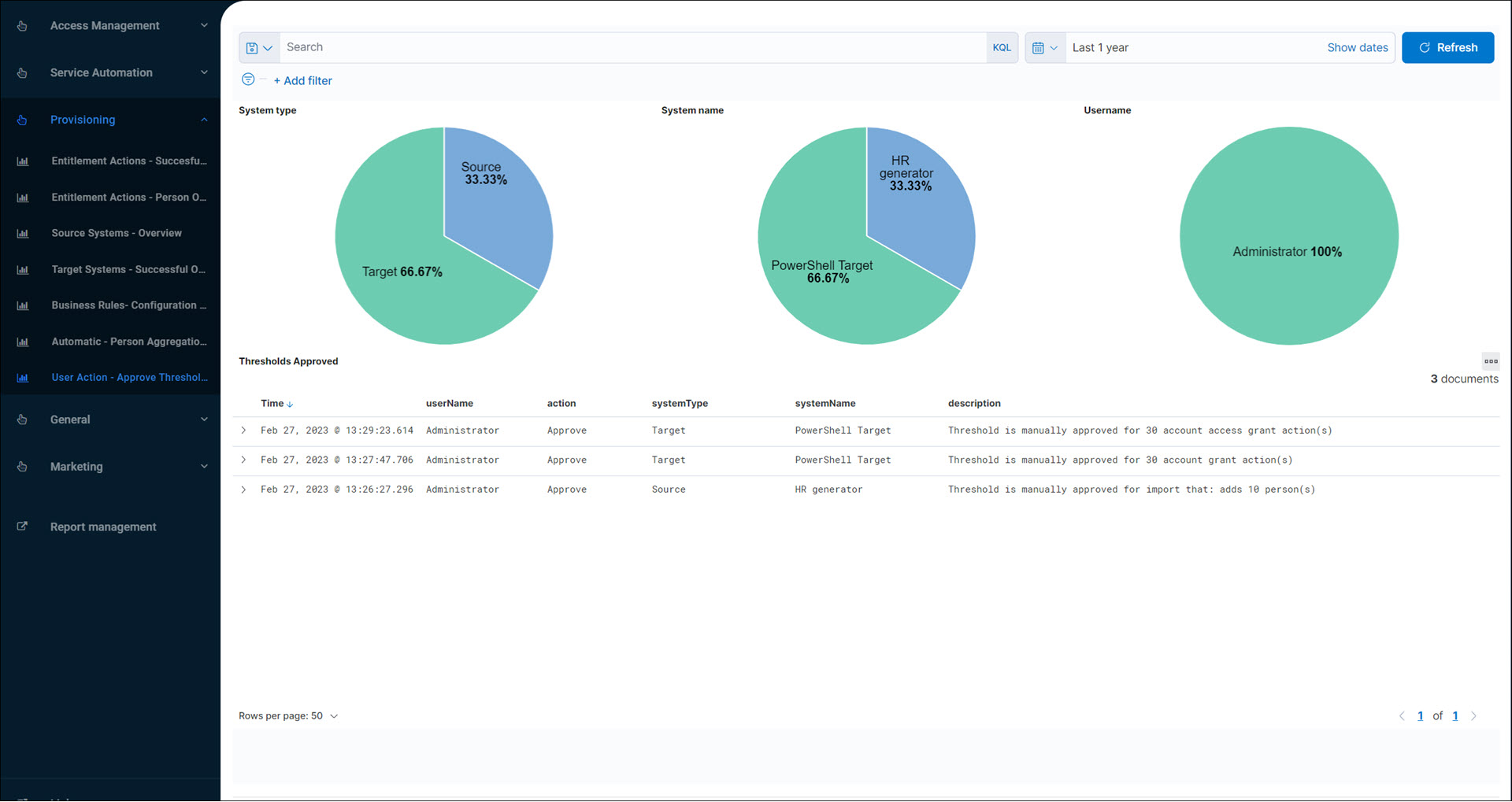
User Action - Approve Thresholds (audit log report)
Shows recently approved Blocked imports (systemType = Source) and recently approved Blocked actions (systemType = Target).
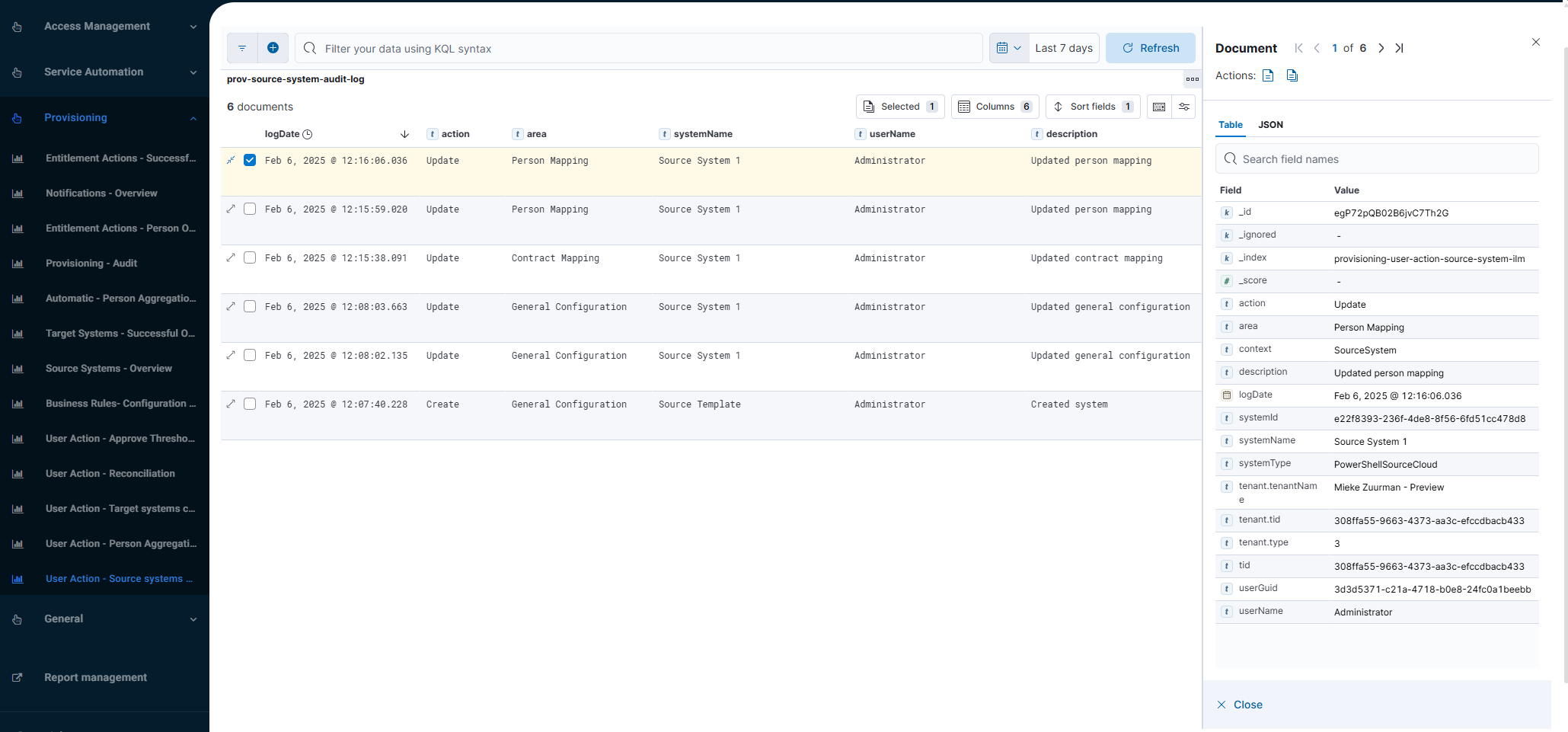
User Action - Source systems changes (audit log report)
Shows changes made to the configuration of provisioning source systems. This includes changes in the system configuration, mapping, person import and department import scripts, and thresholds.
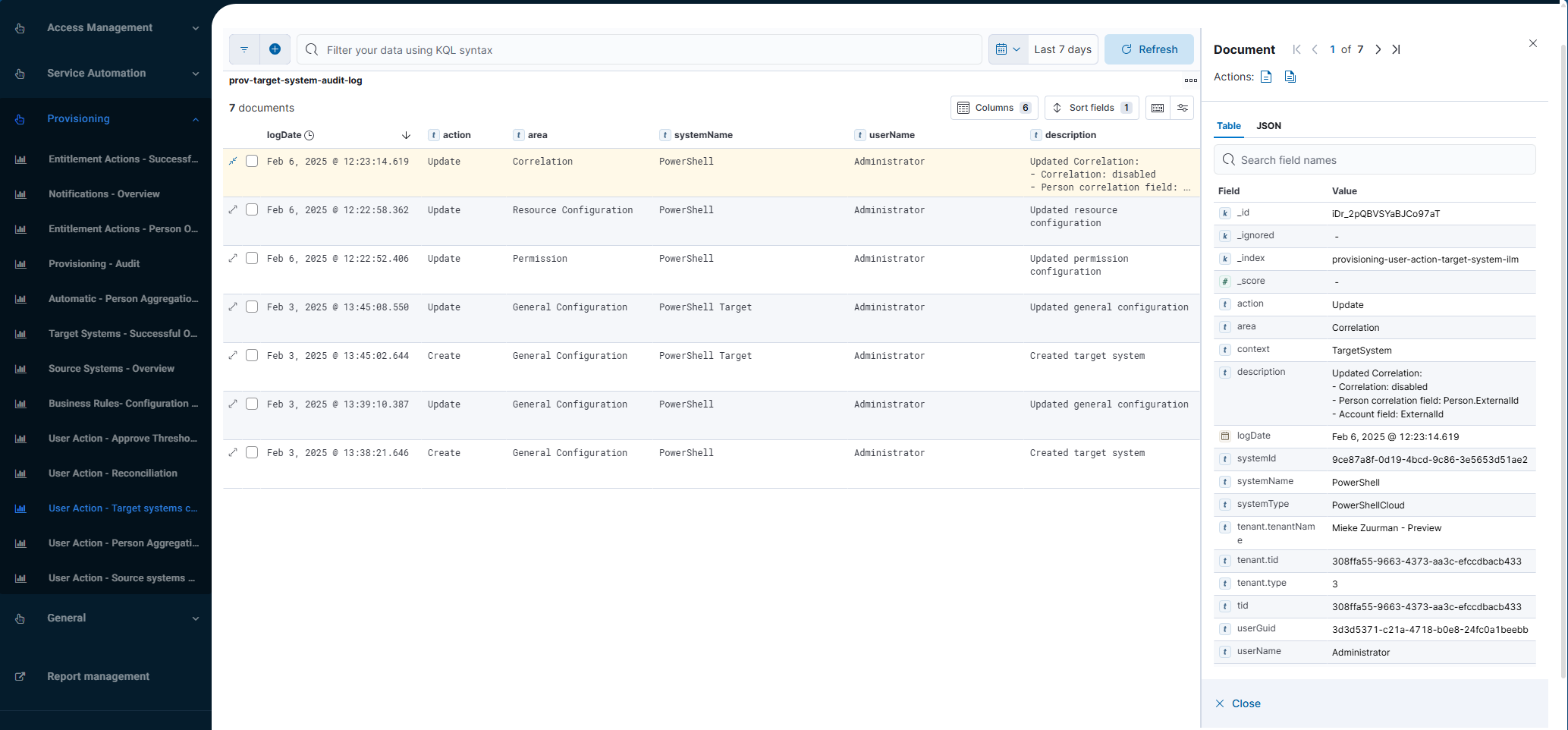
User Action - Target systems changes (audit log report)
Shows changes made to the configuration of provisioning target systems. This includes changes in the system configuration, mapping, resource configuration, scripts, correlation configuration, thresholds, and (for Active Directory target systems) uniqueness validation.
Currently, only Active Directory and PowerShell v2 target systems are included in the report.