Requirements
HelloID requirements are listed below.
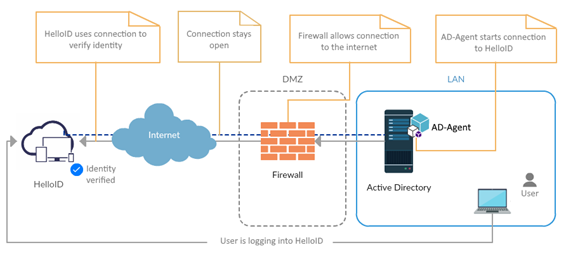
Server
Agent can run on any server in your domain that has HTTPS access to HelloID. We recommend, however, that it be run on a server that is not a domain controller. Running Agent on a domain controller can cause various problems. For example, if the Access Management Agent service starts before the necessary Active Directory services, Agent will be unable to reach AD and will shut down. The On-premises Provisioning Agent service may also encounter conflicts with local security policies.
If you must install Agent on a domain controller, you can attempt to work around these limitations by setting the HelloID Directory Agent to restart on failure in the Recovery tab of its Windows service. You will also need to manually identify and evaluate any security policies which may interfere with the on-premises Provisioning Agent service.
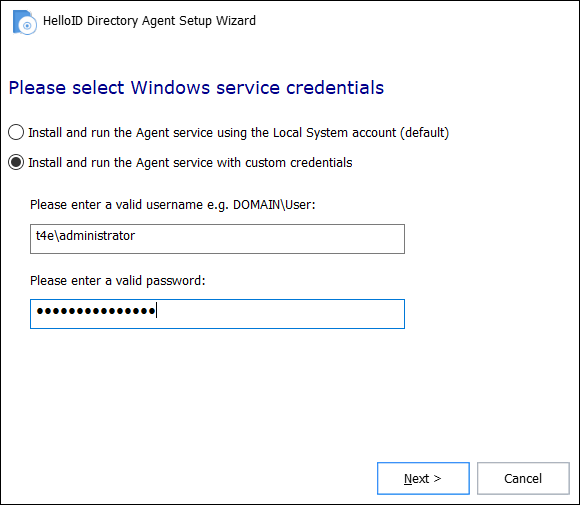
Installation permissions
The HelloID Agent should be installed using a domain account with Local Administrator privileges:
Execution permissions
Once installed, all three On-premises Agent services should also run on a domain account with Local Administrator privileges. Attempting to run the Agent services with a local system account can cause logon problems for end users or failed AD synchronization tasks. Admin privileges are necessary for Agent to auto-update.
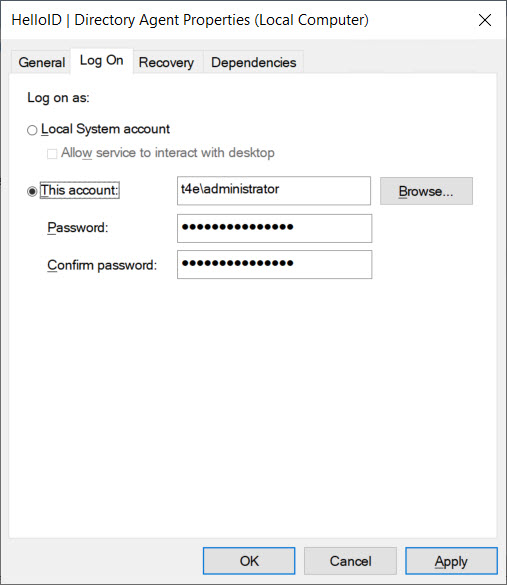
The domain account also needs other permissions depending on the operations that you want to perform in your network. Common permission requirements are listed below.
Synchronizing AD users to HelloID
Read rights for all the Organizational Units above the OU that contains the user accounts and groups that are synced to HelloID.
Read rights for all nested groups of the groups that are synced to HelloID.
Read rights for the following attributes:
Users (Required)
objectSid
userAccountControl
userPrincipalName
sAMAccountName
uSNChanged
Users (Recommended)
Mail
givenName
sn
telephoneNumber
title
department
manager
employeeID
Groups (Required)
objectSid
name
uSNChanged
Groups (Recommended)
ManagedBy
Tasks and other PowerShell scripts
When Agent is used to run a task from the HelloID Task catalog, any required PowerShell modules must be installed on the server running the Agent. Required modules are displayed alongside each task in the task catalog. For example:

For custom PowerShell tasks, PowerShell data sources, and Delegated form PowerShell scripts, you must manually determine & assign the needed permissions.
Minimum Hardware
1 vCPU
4 GB RAM
500 MB free disk space
Recommended Hardware
4 vCPU
8 GB RAM
1 GB free disk space
Software
Windows Server 2019 or higher (older editions may work, but we recommend staying within the Microsoft Lifecycle Policy)
PowerShell version 5 or higher
Note
If you have installed more than one Agent, all Agents must be running on the same version of PowerShell.
.NET Framework 4.8.0 or higher
Firewall
The server(s) running Agent need to have access to the HelloID platform to ensure working communication for the user synchronization, authentication, and automation tasks. All traffic is initiated by Agent itself using HTTPS port 443. No inbound ports need to be allowed on the firewall. You must also set up a Whitelist domains. The level of encryption is TLS 1.2, AES, with 256-bit encryption.
Antivirus and antimalware
The HelloID Agent services must be excluded from any antivirus and/or antimalware software.
All three services should be explicitly listed as exclusions.
Additionally, it might be helpful to include a folder exclusion for the following paths:
C:\ProgramData\Tools4ever
C:\Program Files\Tools4ever
Recommended browser: Mozilla Firefox or Google Chrome.
Internet Explorer is not supported.
The AD (SAML) IdP is a simple, free alternative IdP for organizations which don't use Active Directory Federation Services. It provides pass-through authentication for HelloID via SAML.
It’s not necessary to make the AD IdP available to the internet since all actions are initiated by the user’s browser client.
The AD IdP can be installed multiple times in one configuration to ensure high availability. If a high availability setup is needed, this has to be configured by the customer using their own preferred solution.
The AD IdP server must be configured with an SSL Certificate in IIS, which must be trusted by the client machines. The traffic to the HelloID webserver is using HTTPS. The level of encryption is TLS 1.2, AES with 256-bit encryption.
The following attributes will be sent in the SAML Message:
SAML Attribute | Example |
|---|---|
NameID | DOMAIN\Username |
user@helloid.com | |
FirstName | John |
LastName | Williams |
ADSID | S-1-5-21-1085031214-1563985344-725345543 |
ADUPN | user@helloid.com |
ADPhone | +31 6 123456789 |
It is not possible to change this default attribute set.
Hardware
4 GHz 64-bit processor or faster
2 GB of RAM or more
10MB program, 200MB data diskspace
Software
Windows server 2012 R2 or newer
.NET Framework 4.5
Web Server (IIS)
Common HTTP Features
Default Document
Directory Browsing
HTTP Errors
Static Content
Health and Diagnostics
HTTP Logging
Performance
Static Content Compression
Security
Request Filtering
Windows Authentication (not selected by default)
Application Development
.NET Extensibility 4.5 (not selected by default)
.NET 4.5 (not selected by default)
ISAPI Extensions (not selected by default)
ISAPI Filters (not selected by default)
Management Tools
IIS Management Console
SSL Webserver certificate
Windows
Internet Explorer | Version 9 and higher |
Chrome | Version 18 and higher |
Firefox | Version 21 and higher |
Edge | Does not support plugins |
Opera | Not supported |
Mac
Chrome | Version 18 and higher |
Firefox | Version 21 and higher |
Safari | Not supported |
Mobile devices
iOS | Version 9 and higher |
Android | Version 4.4 and higher |
AD connector for HelloID
Windows Server | 2003 and higher |
AD IdP
Windows Server | 2008 SP2 and higher |
.NET Framework | 4.5 and higher |